版本:12.5
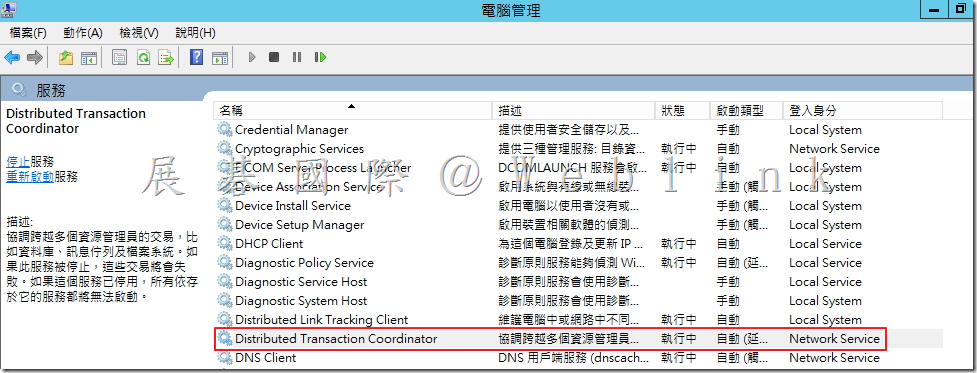
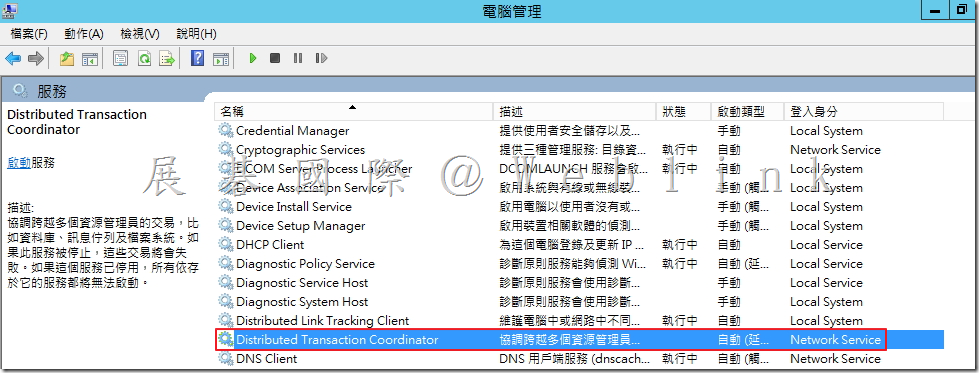
1. 在 Windows 服務中,如果正在執行以下服務,請將其停止:
- 所有 Oracle 服務
- Distributed Transaction Coordinator 服務
2. 準備安裝 Oracle 檔案。
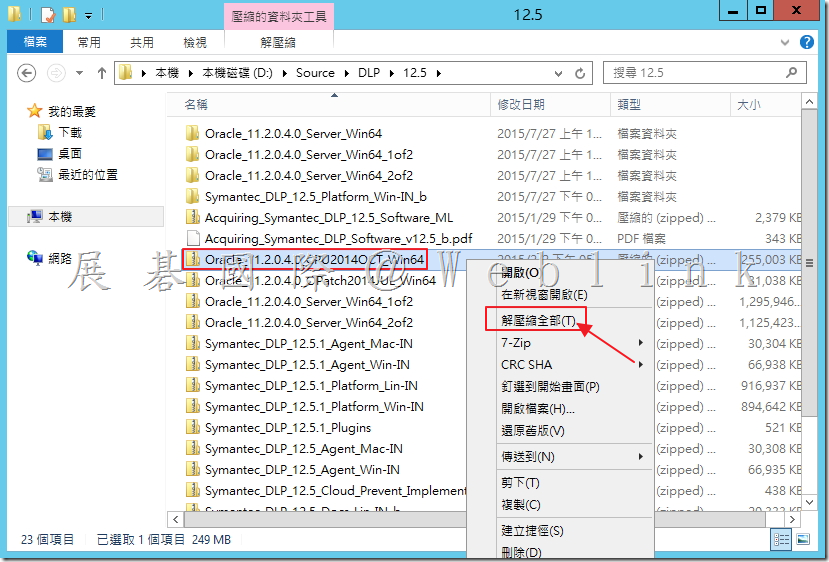
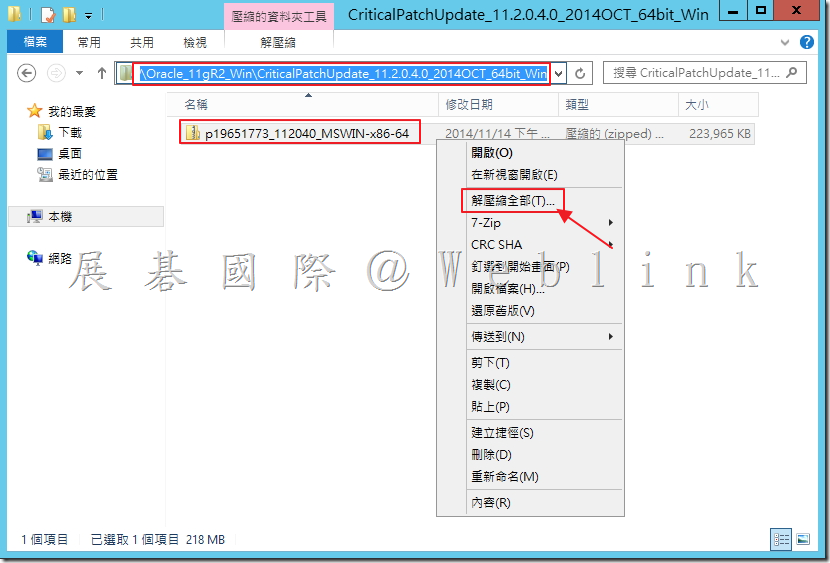
2.1 解壓縮下載下來的【Oracle_11.2.0.4.0_Server_Win64_1of2.zip】與【Oracle_11.2.0.4.0_Server_Win64_2of2.zip】。
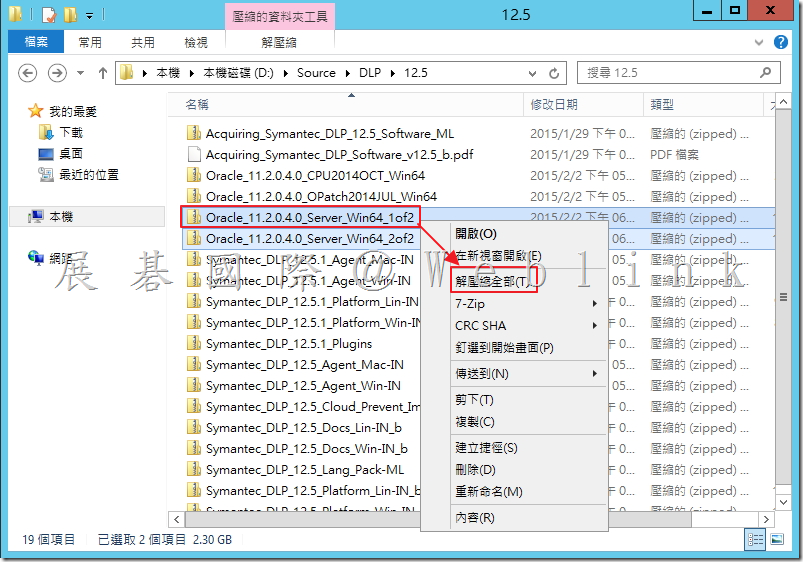
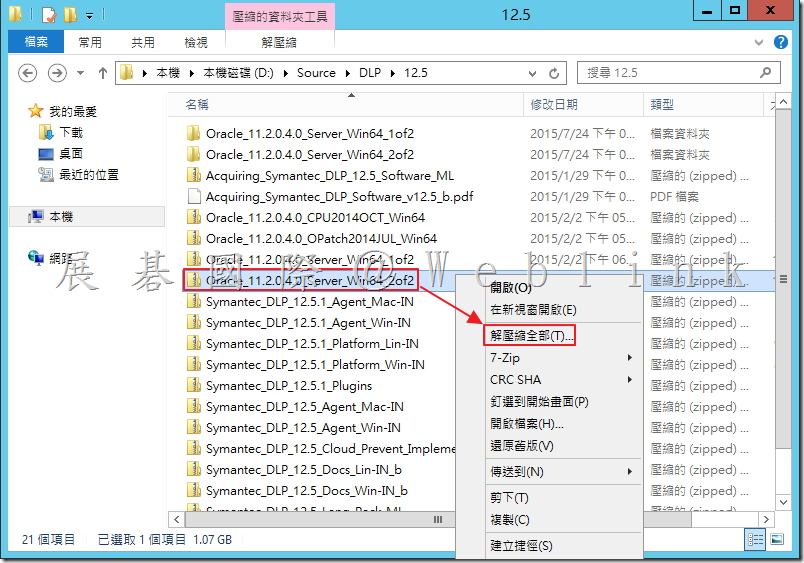
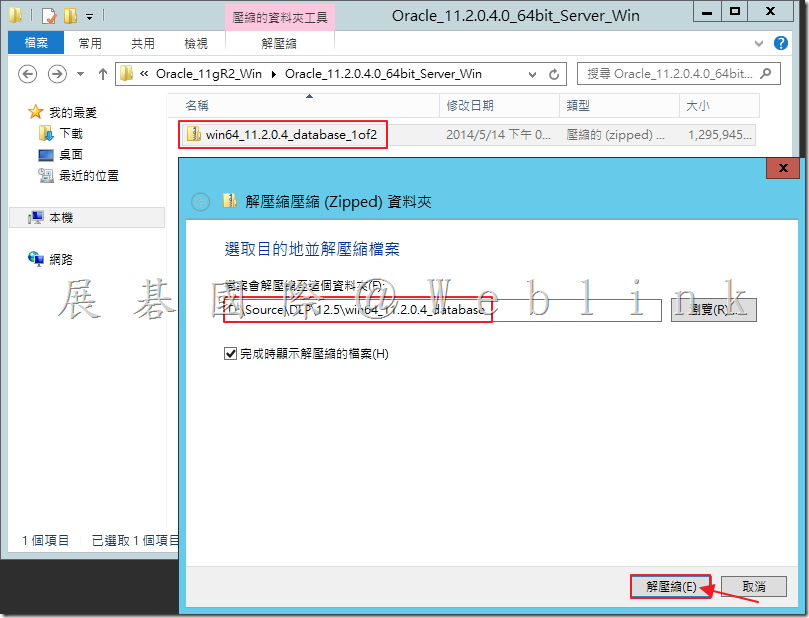
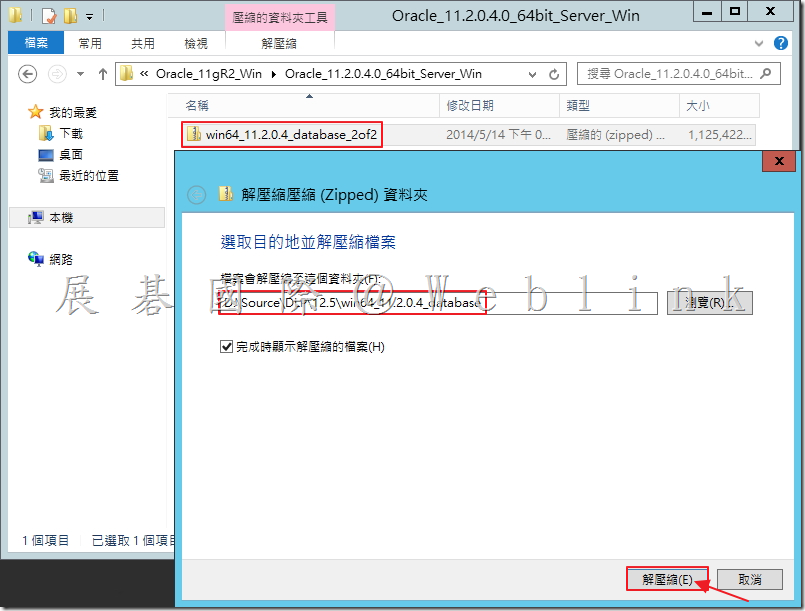
2.2 將 2.1 所解壓縮後的檔案「win64_11.2.0.4_database_1of2.zip」與「win64_11.2.0.4_database_2of2.zip」解壓縮後的檔案放至同個資料夾內。
2.3 解壓縮後可至剛剛選取的資料夾看到以下檔案。
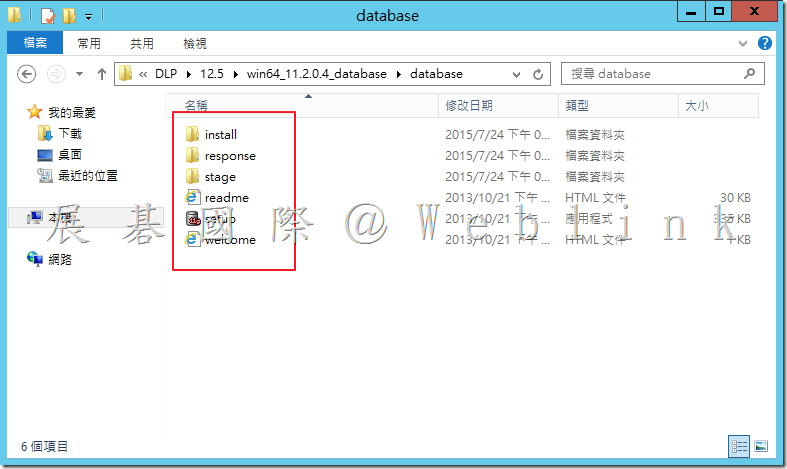
3. 安裝 Oracle
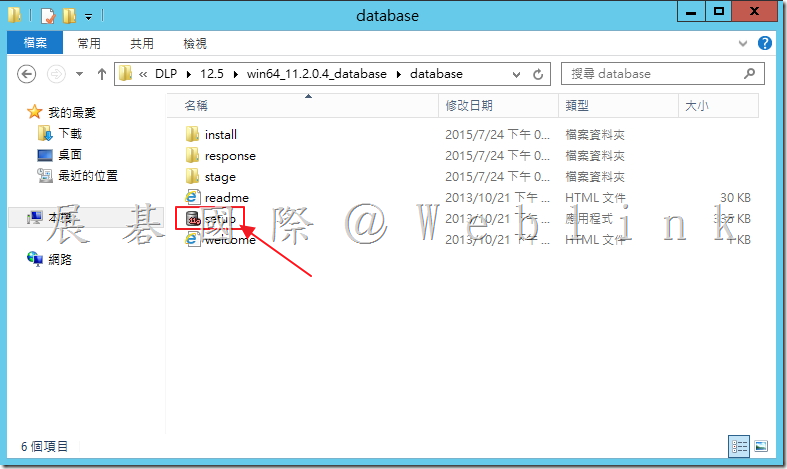
3.1 執行「setup」。
3.2 檢查顯示器。
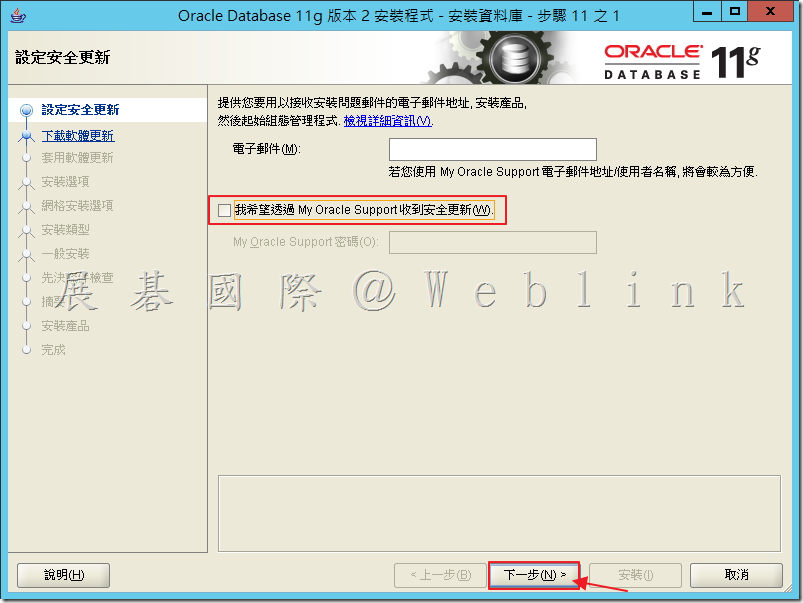
3.3 取消勾選「我希望透過My Oracle Support收到安全更新」,接著點選「下一步」。
3.4 點選「是」。
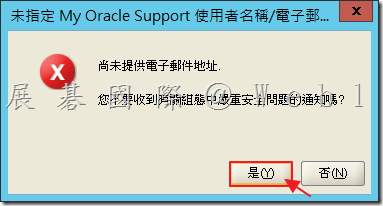
3.5 選取「略過軟體更新」,接著點選「下一步」。
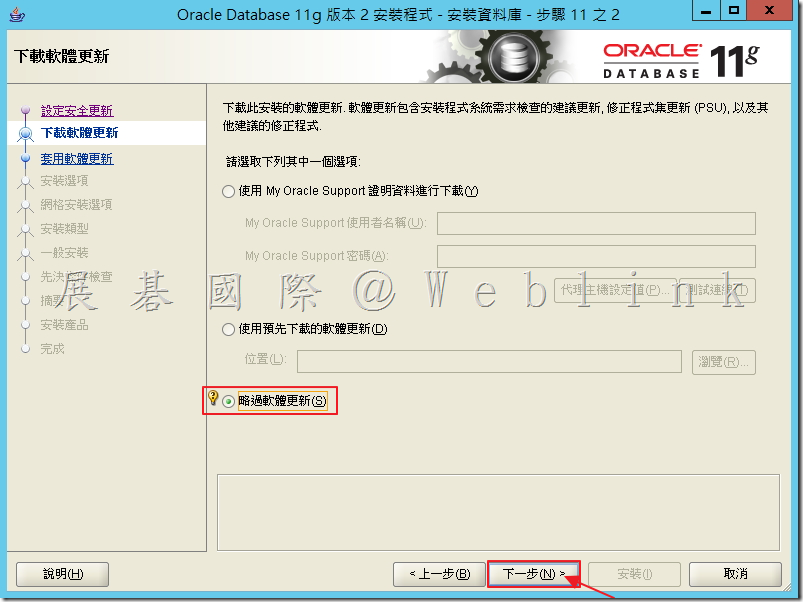
3.6 點選「只安裝資料庫軟體」,接著點選「下一步」。
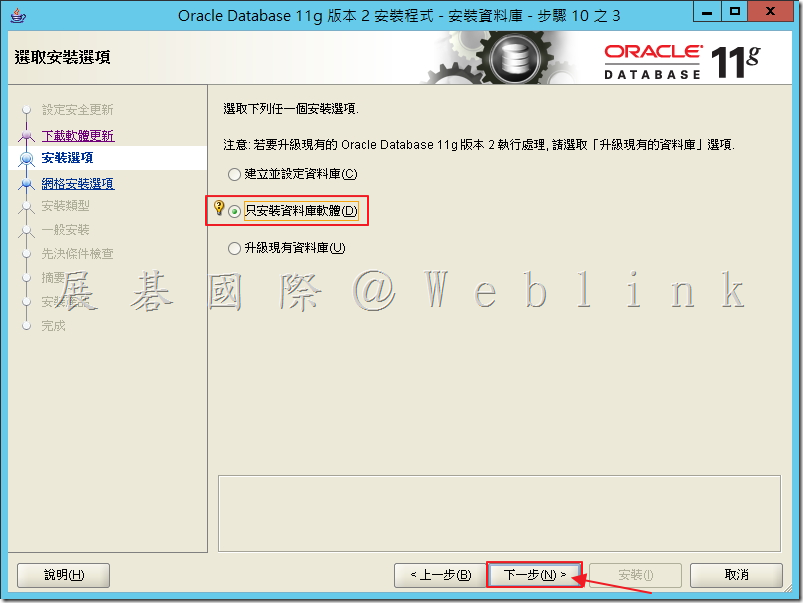
3.7 點選「單一執行處理資料庫安裝」,接著點選「下一步」。
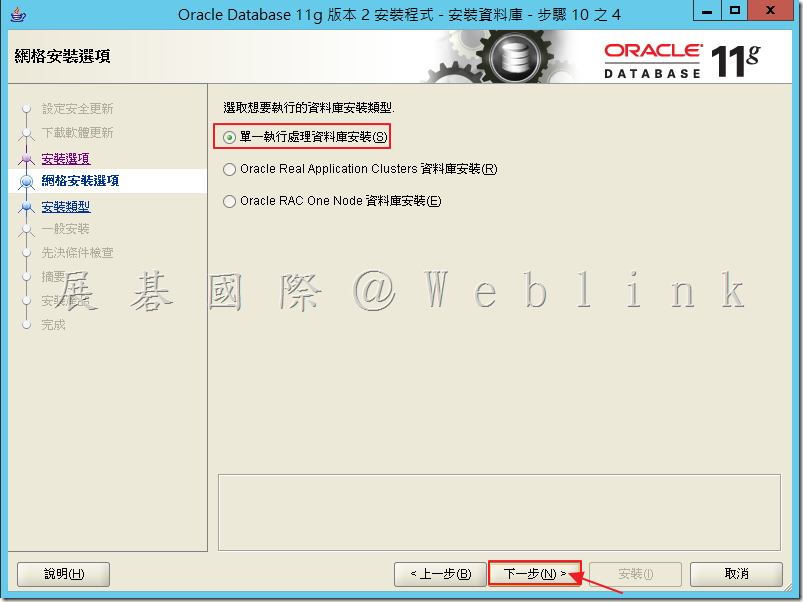
3.8 確認語言「繁體中文」和「英文」,接著點選「下一步」。
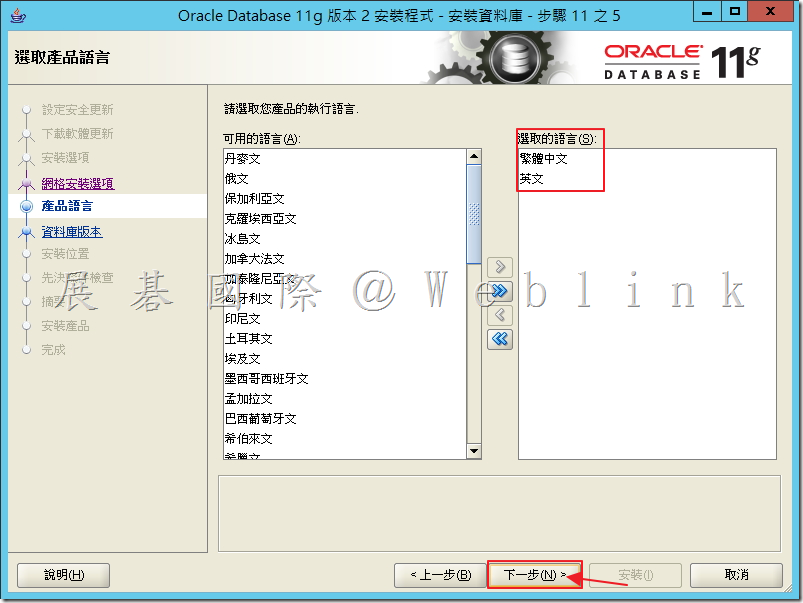
3.9 選取「Standard Edition ( 3.7 GB )」,接著點選「下一步」。
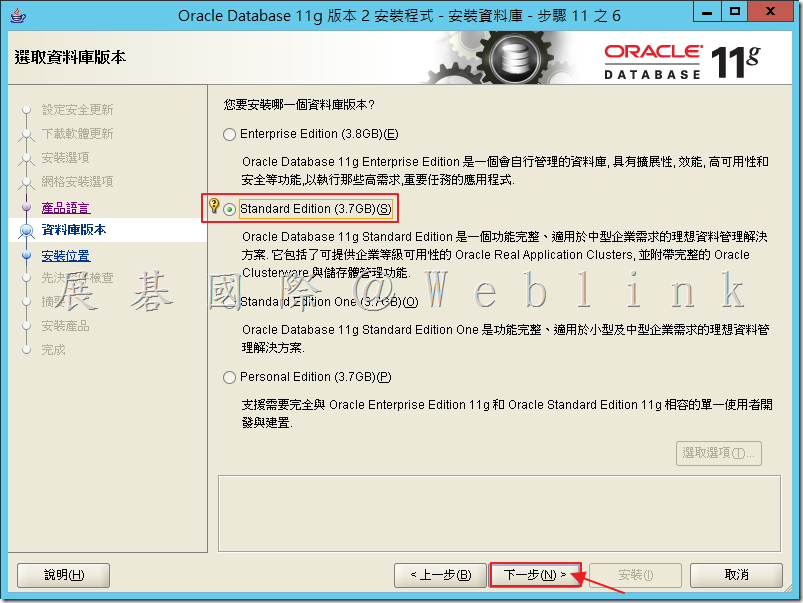
3.10 修改安裝路徑。
C:\app\Administrator → C:\oracle
C:\app\Administrator\product\11.2.0\dbhome_1→C:\oracle\product\11.2.0\dbhome_1
3.11 安裝先決條件檢查。
3.12 確認安裝資訊無誤,點選「安裝」。
3.13 安裝中。
3.14 安裝完成,點選「關閉」。
4. 建立 Symantec Data Loss Prevention 資料庫
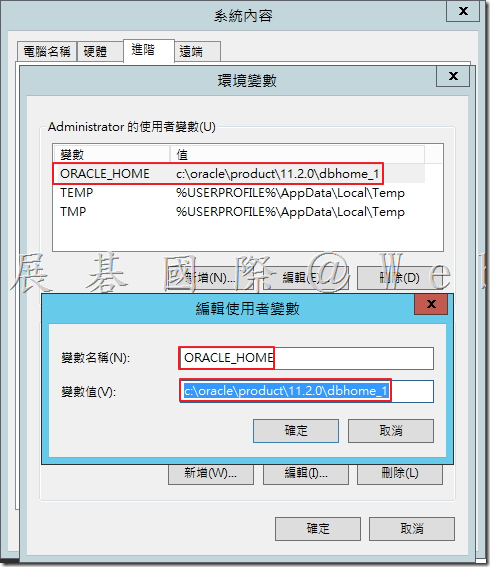
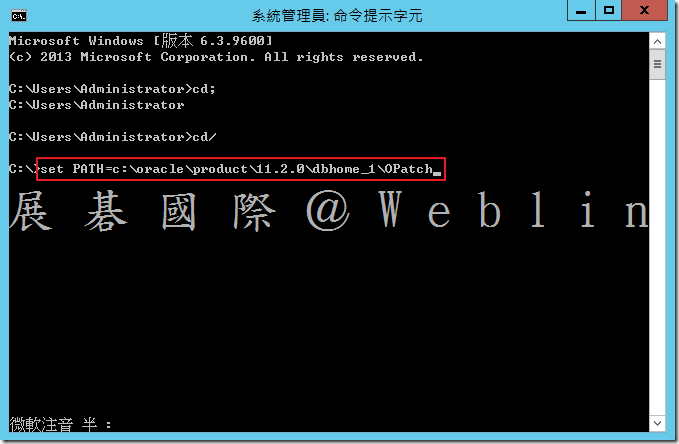
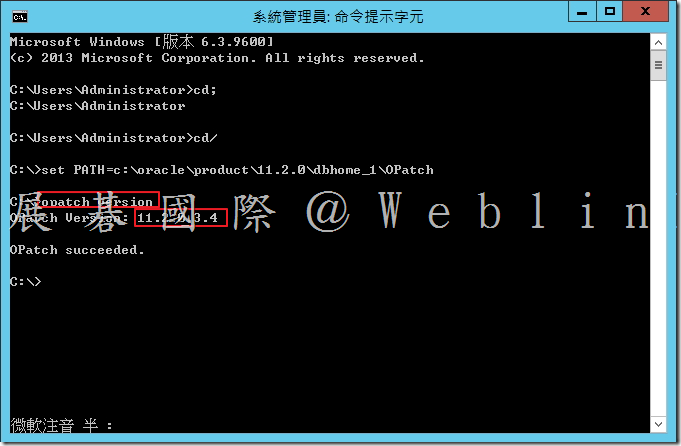
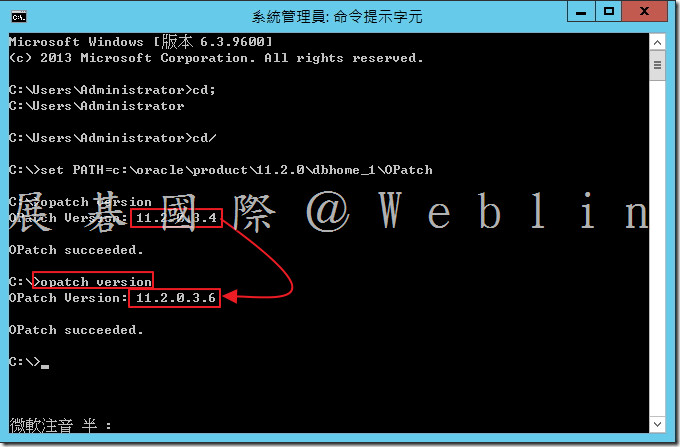
4.1 設定 ORACLE_HOME 環境變數
C:\oracle\product\11.2.0\dbhome_1
4.2 準備資料庫檔案。
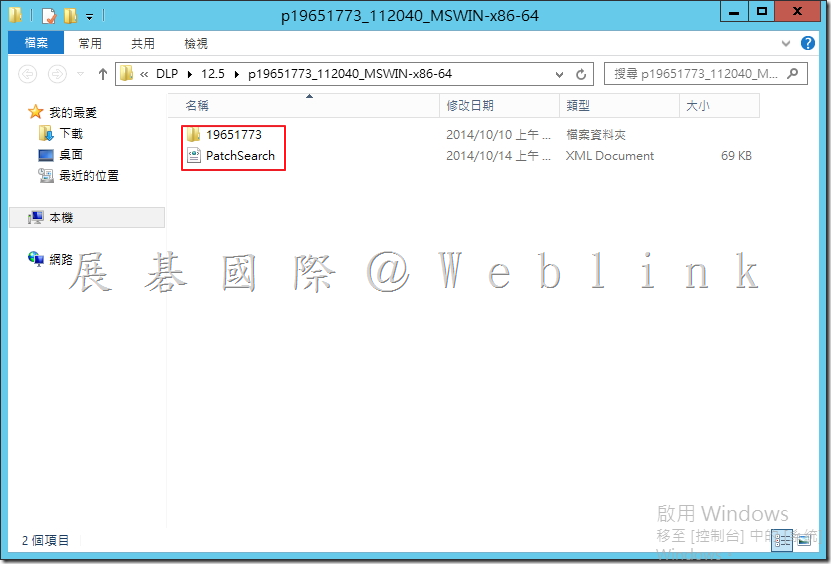
4.2.1 解壓縮Symantec_DLP_12.5_Platform_Win-IN_b.zip。
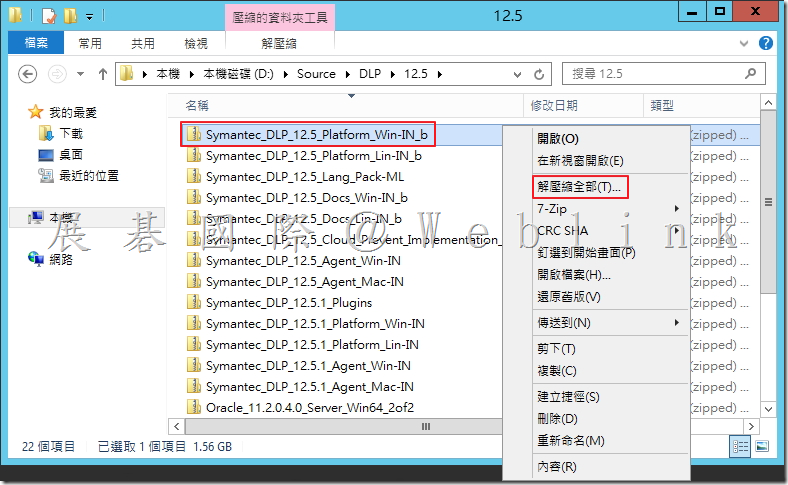
4.2.2 開啟「New_Install」資料夾。
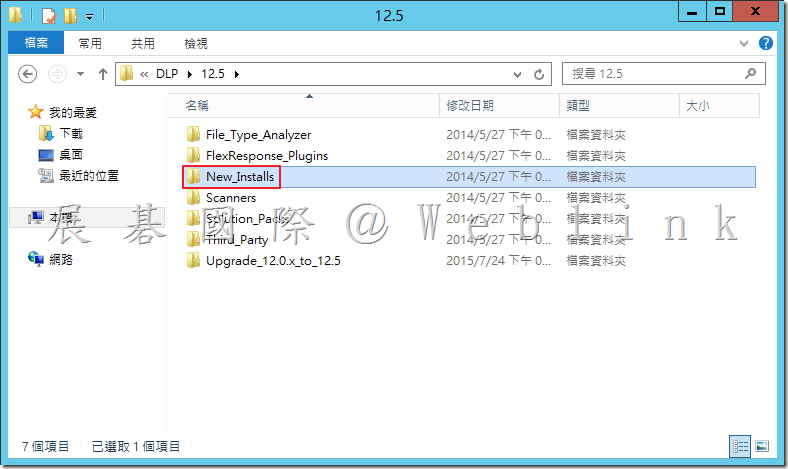
4.2.3 開啟「Oracle_Configuration」資料夾。
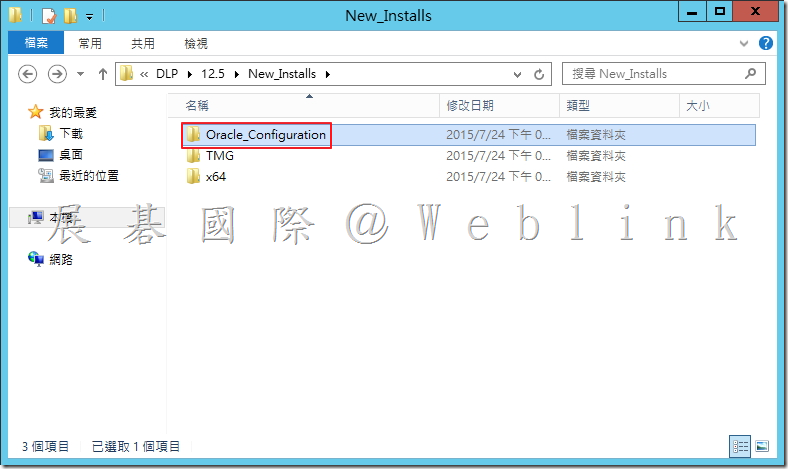
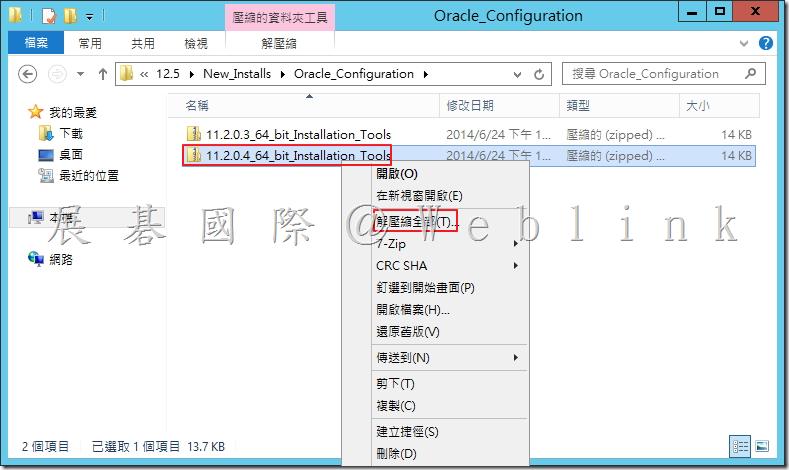
4.2.4 解壓縮「11.2.0.4_64_bit_Installation_Tools.zip」。
4.2.5 將 Oracle_11.2.0.4_Template_for_DLP_v12.5_64_bit_WIN.dbt 複製到「C:\oracle\product\11.2.0\dbhome_1\assistants\dbca\templates」
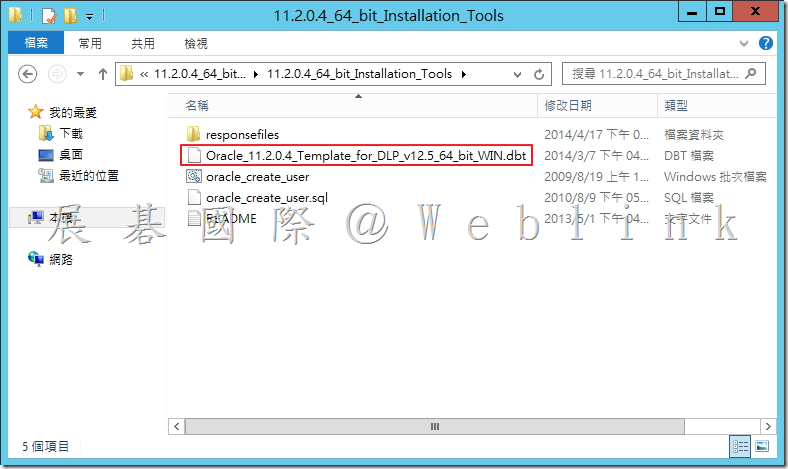
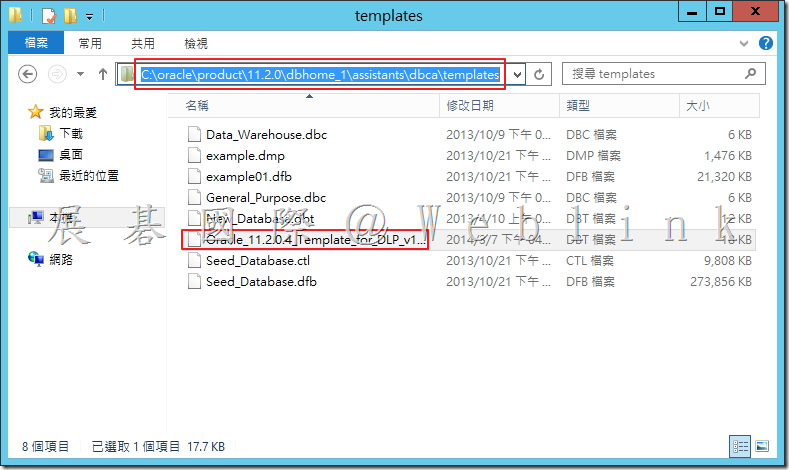
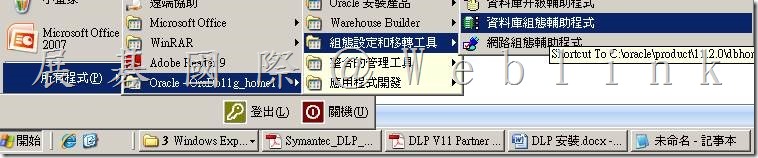
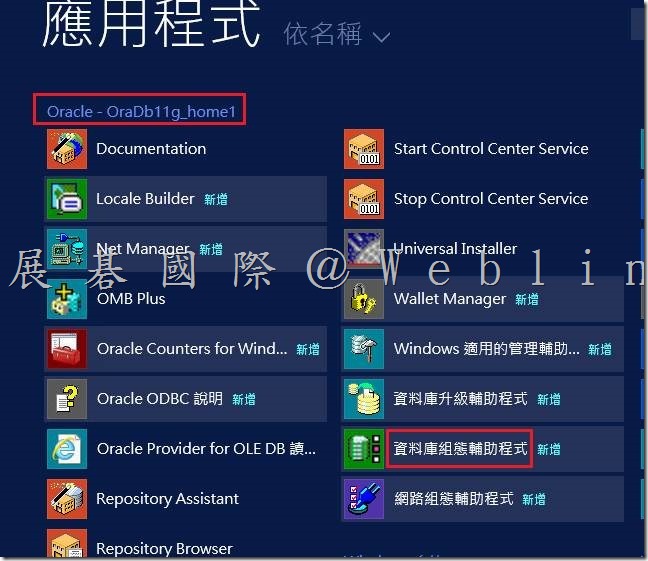
4.3 啟動 Oracle 資料庫組態輔助程式以建立 Symantec Data Loss Prevention 資料庫。
選擇「開始」>「所有程式」> Oracle – OraDb11g_home1 >「組態設定和移轉工具」>「資料庫組態輔助程式」
Windows server 2012 R2
4.4. 點選「下一步」。
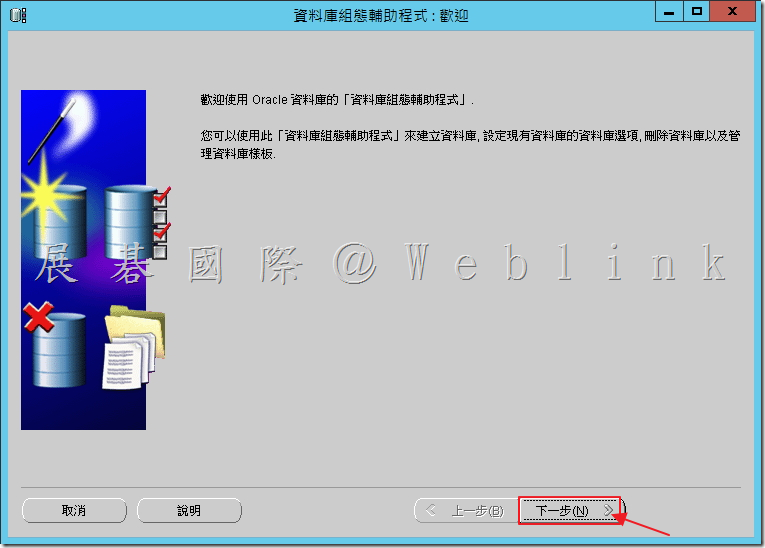
4.5 點選「建立資料庫」,接著點選「下一步」。
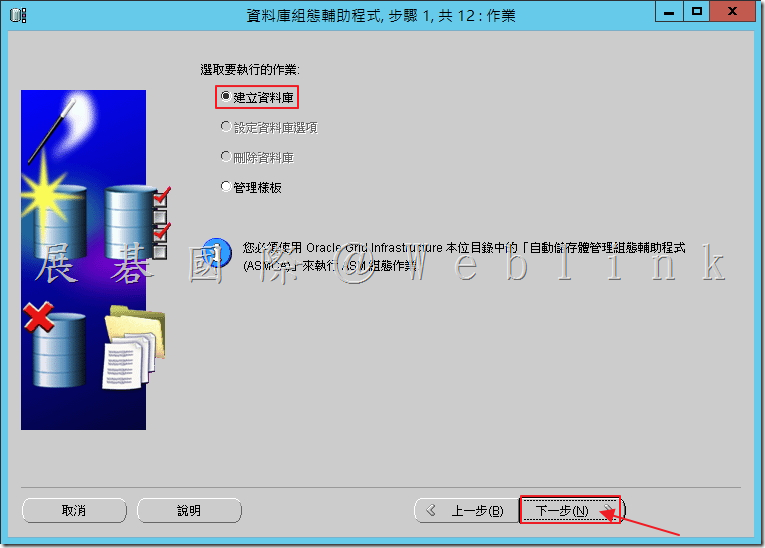
4.6 選取「Oracle 11.2.0.4 Template for DLP v12.5 64 bit WIN」,接著點選「下一步」。
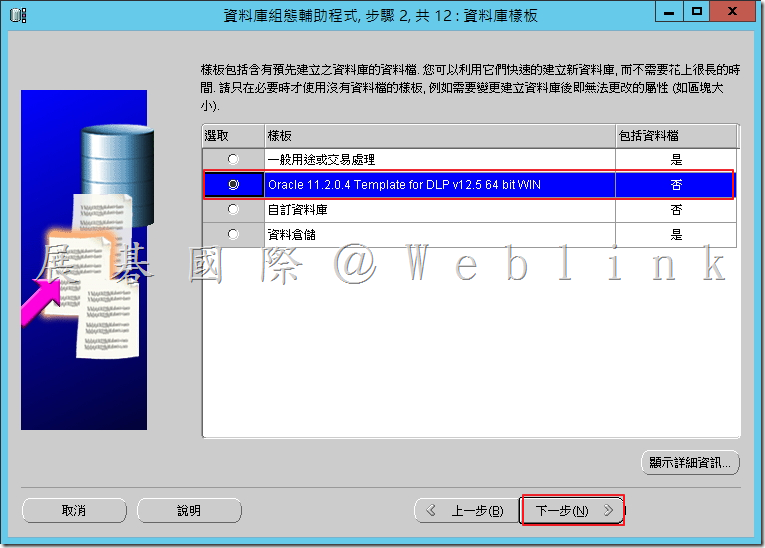
4.7 輸入並記錄資料庫名稱和SID,稍後在安裝Symantec Data Loss Prevention軟體時會用到這些資訊,接著點選「下一步」。
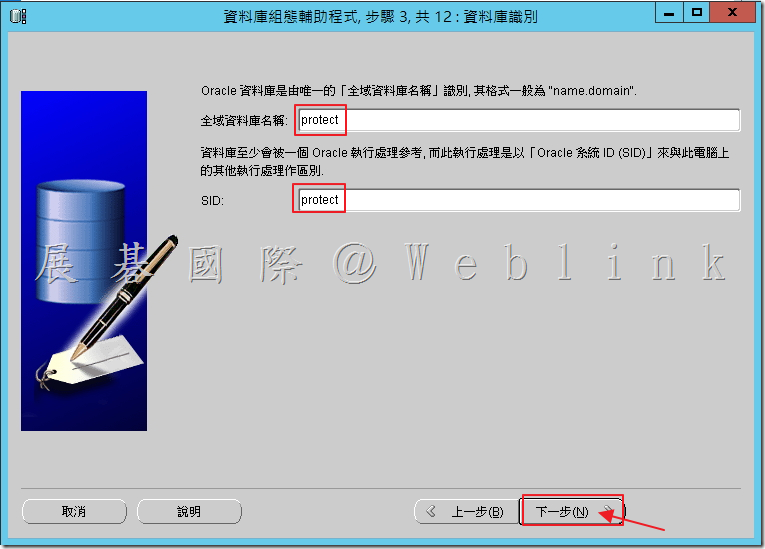
4.8 於「Enterprise Manager」取消選取「設定 Enterprise Manager」。
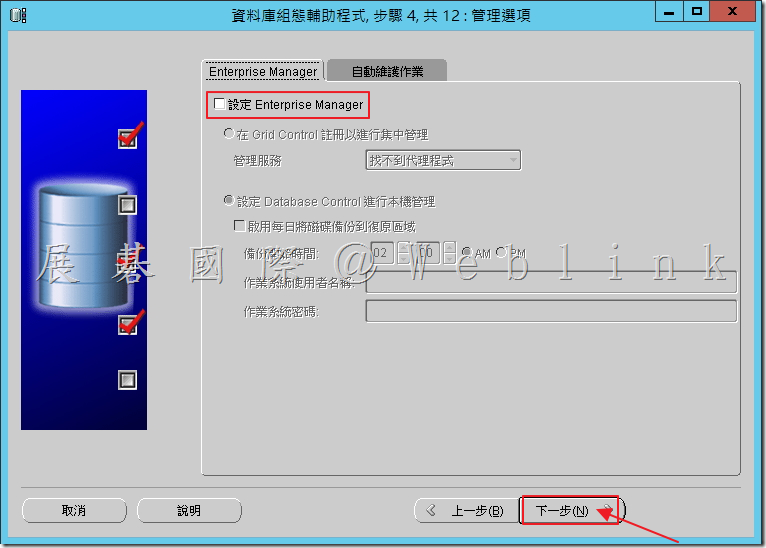
4.9 於「自動維護作業」取消選取「啟用自動維護作業」。
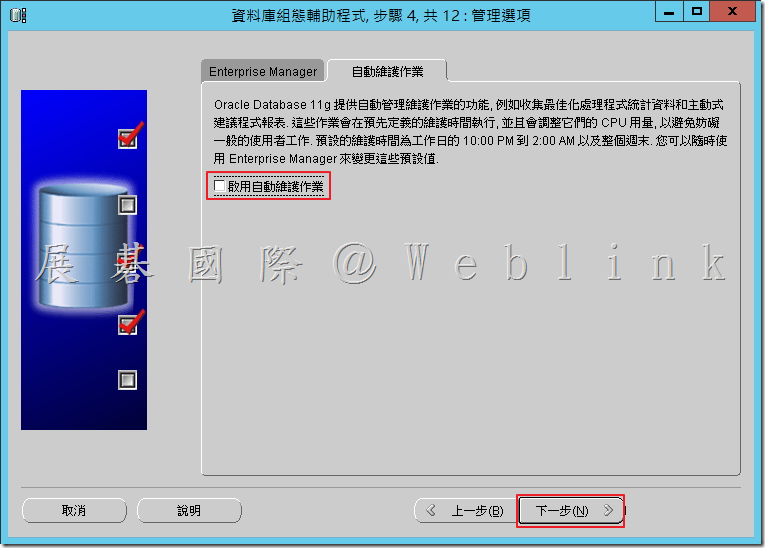
4.10 選取「所有帳戶使用相同管理員密碼」,在「密碼」欄位中輸入密碼(Passw0rd)在「確認密碼」欄位中重新輸入相同密碼,接著點選「下一步」。
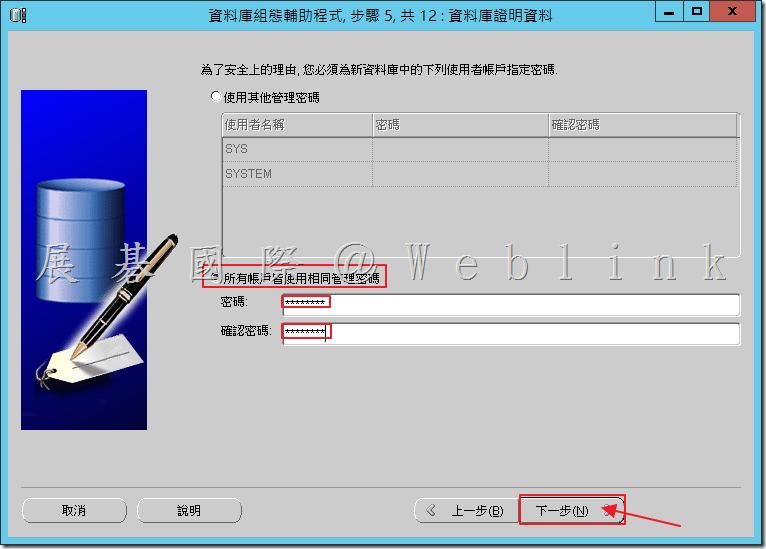
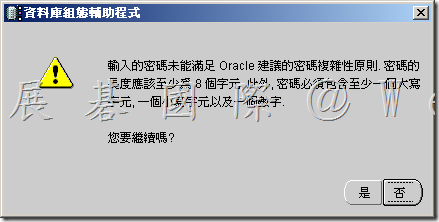
請遵循以下規範來建立可接受的密碼:
- 密碼不得包含引號。
- 密碼不區分大小寫。
- 密碼必須以字母字元開頭。
- 密碼只能包含英數字元。請勿在密碼中使用底線(_)、美元符號($) 及井字符號(#),因為Oracle 解釋這些符號的方式不同於其他系統。
- 密碼不得為 Oracle 保留字,例如 SELECT。
- 如果您輸入的密碼不符合上述規範,Oracle 會繼續提示您提供密碼。您必須輸入密碼。請勿刪除Oracle 資料庫組態輔助程式。
4.11 點選「完成」。
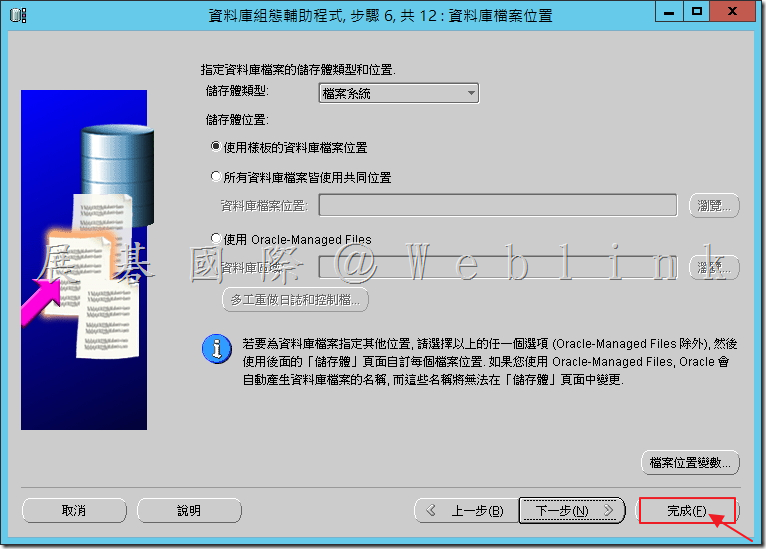
4.12 設定完成,點選「確定」。
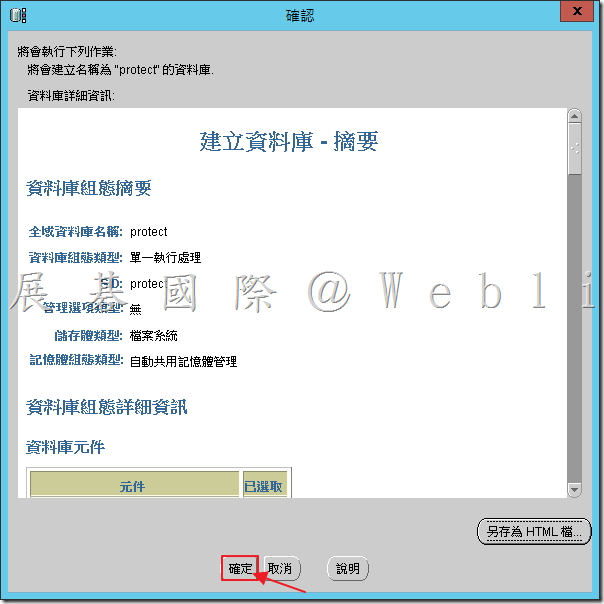
4.13 資料庫建立中。
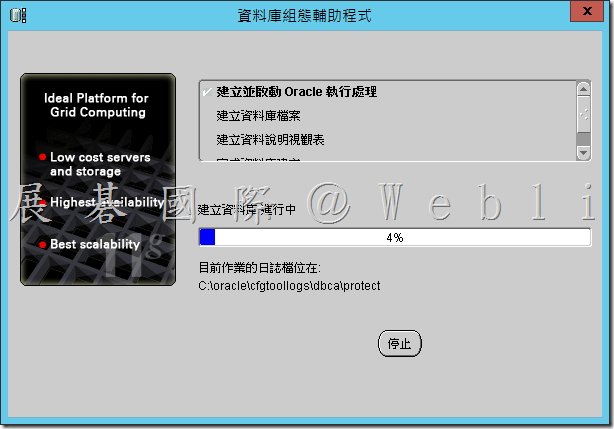
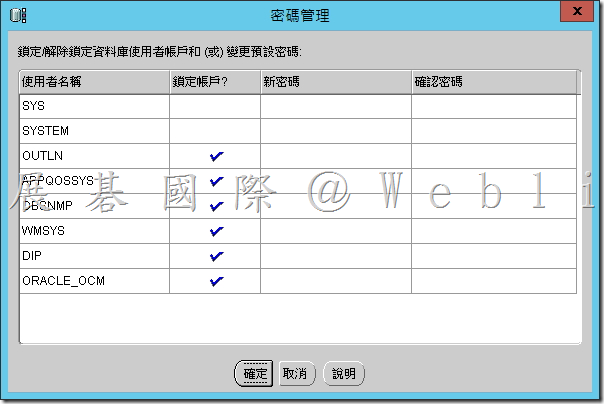
4.14 資料庫建立完成,接著點選「密碼管理」。
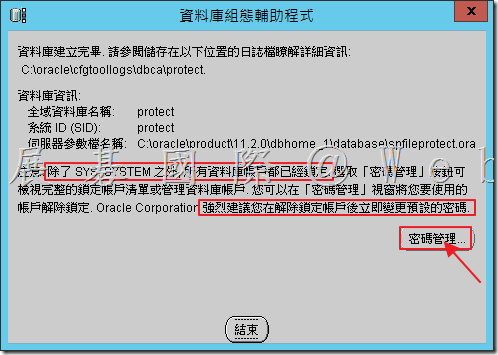
4.15 可看到目前設定的帳戶及密碼,接著點選「確定」。
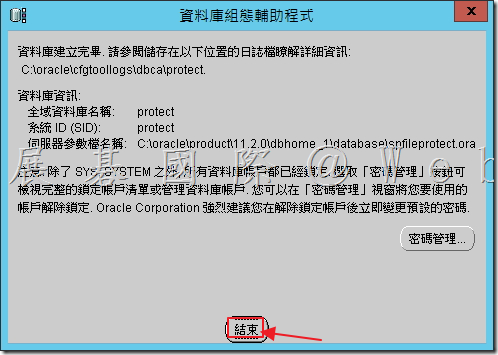
4.16 最後點選「結束」。
※除錯方式
如果資料庫建立程序失敗或當機,請檢查 Oracle 資料庫組態助理日誌 (位於 %ORACLE_HOME%\cfgtoollogs\dbca\SID 資料夾) 中的錯誤
(例如 C:\app\Administrator\product\11.2.0\dbhome_1\cfgtoollogs\dbca\protect)
![clip_image002[1] clip_image002[1]](http://www.wellife.com.tw/symantec/wp-content/uploads/sites/4/2015/07/clip_image0021_thumb.jpg)
Windows server 2012 R2
5. 在 Windows 上建立 TNS 監聽程式
如果以網域使用者身分登入,則必須將 sqlnet.ora 檔案中的
SQLNET.AUTHENTICATION_SERVICES=() 值設定為 none。否則,請移至步驟2。
若要設定 sqlnet.ora 檔案的 SQLNET.AUTHENTICATION_SERVICES=() 值,請依序執行以下步驟:
- 使用文字編輯器,開啟位於 %Oracle_Home%networkadmin 資料夾(例如 C:\oracle\product\11.2.0\dbhome_1\NETWORK\ADMIN)的 sqlnet.ora。
- 將 SQLNET.AUTHENTICATION_SERVICES=(NTS) 值變更為 none。 SQLNET.AUTHENTICATION_SERVICES=(none)
- 儲存並關閉 sqlnet.ora 檔案
5.1 執行網路組態輔助程式。
Windows server 2012 R2
![clip_image004[1] clip_image004[1]](http://www.wellife.com.tw/symantec/wp-content/uploads/sites/4/2015/07/clip_image0041_thumb.jpg)
5.2 選取「監聽器組態」,接著點選「下一步」。
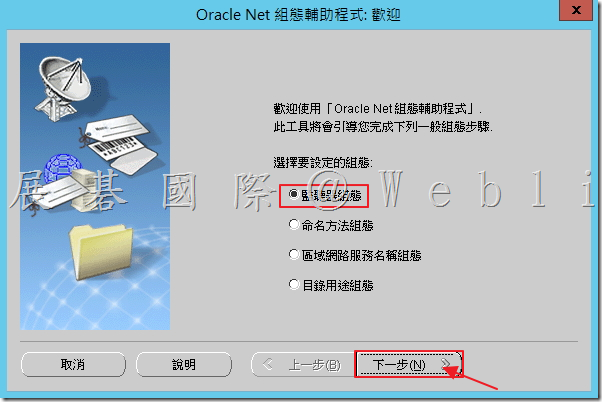
5.3 選取「新增」,接著點選「下一步」。
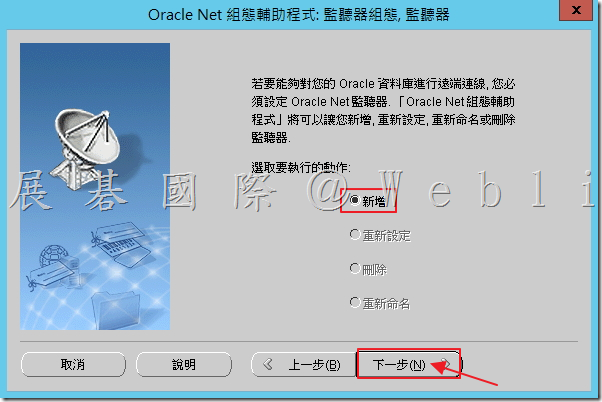
5.4 使用預測「監視器名稱:LISTENER」,接著點選「下一步」。
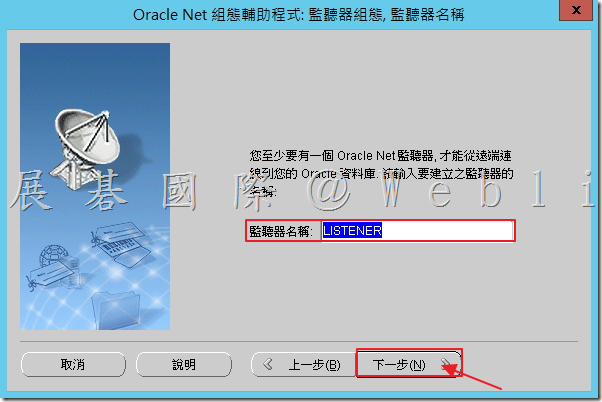
5.5 選取協定「TCP」,接著點選「下一步」。
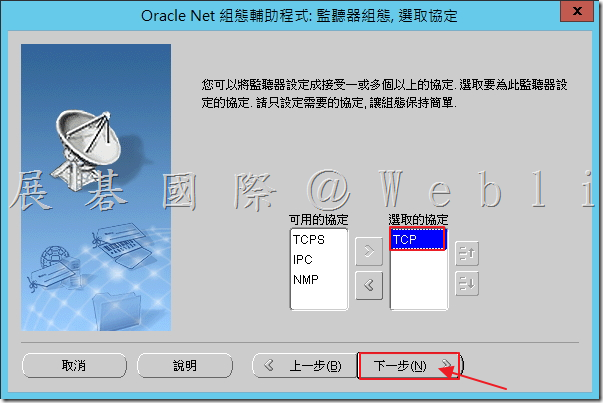
5.6 選取「使用 1521 標準連接埠號碼」,接著點選「下一步」。
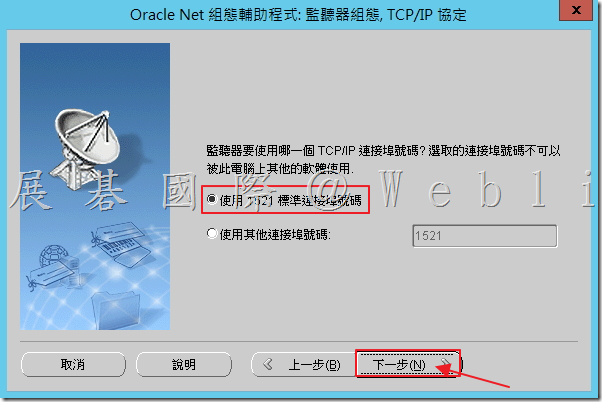
5.7 選取「否」,接著點選「下一步」。
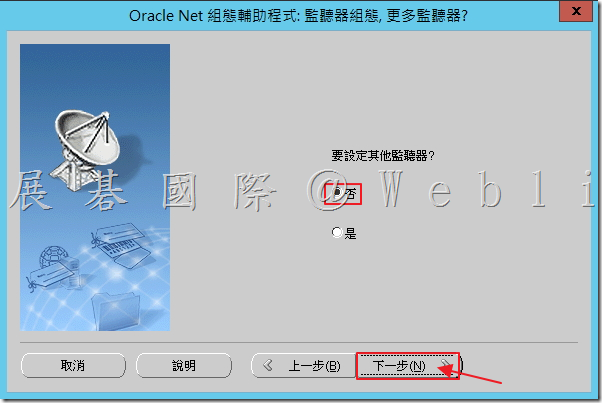
5.8 監聽器組態完成,接著點選「下一步」。
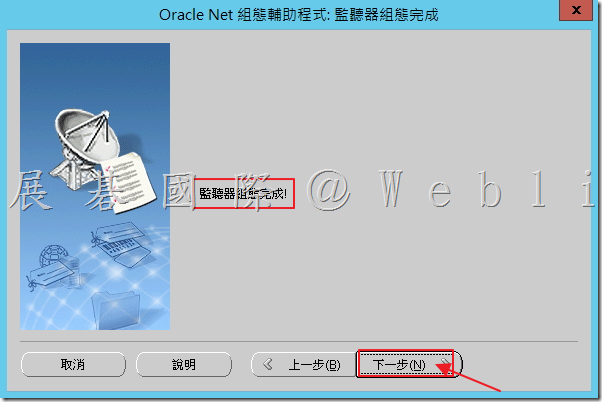
6. 為 Symantec Data Loss Prevention 資料庫架構本機網路服務名稱
6.1 點選「區域網路服務名稱組態」,接著點選「下一步」。
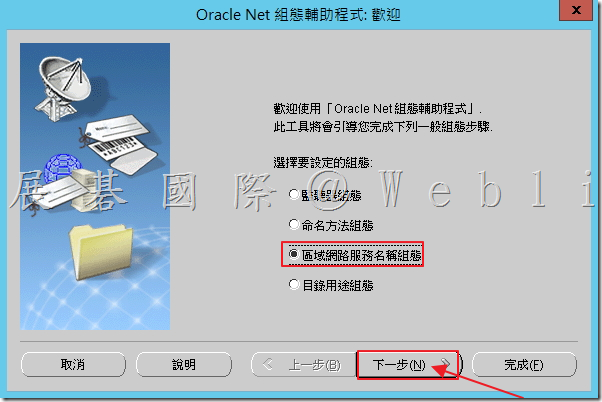
6.2 點選「新增」,接著點選「下一步」。
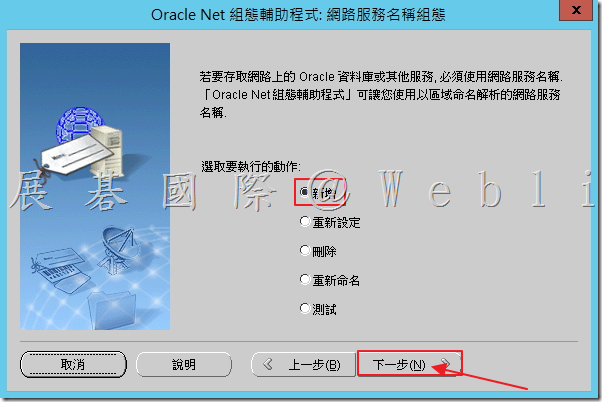
6.3 輸入 Oracle 服務名稱,接著點選「下一步」。
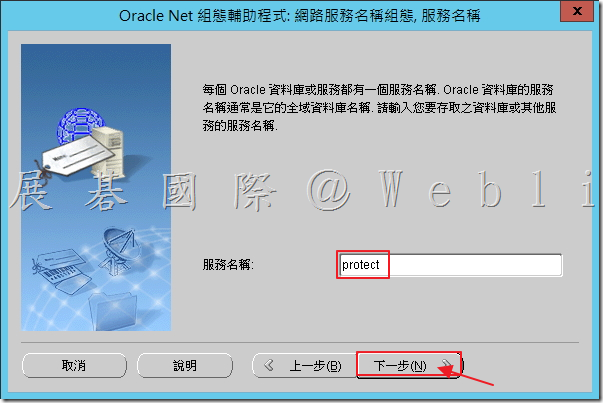
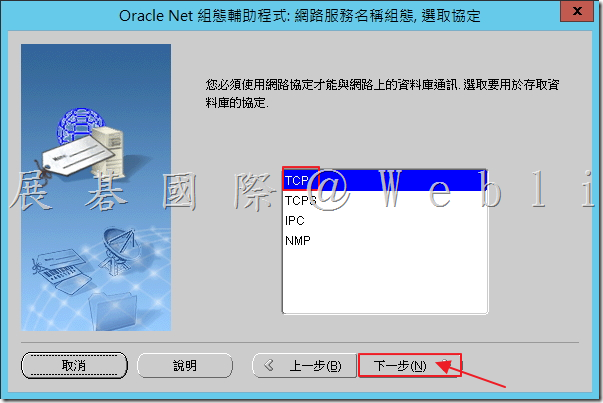
6.4 選取「TCP」,接著點選「下一步」。
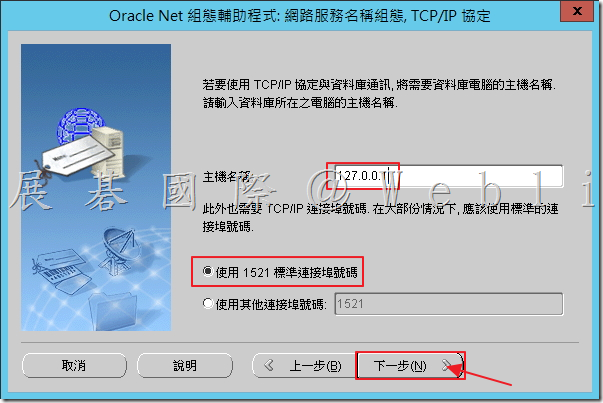
6.5 輸入「主機名稱」,接著點選「使用1521標準連接埠號碼」,最後點選「下一步」。
6.6 由於尚未啟動監聽程式,因此點選「否,不執行測試」,接著點選「下一步」。
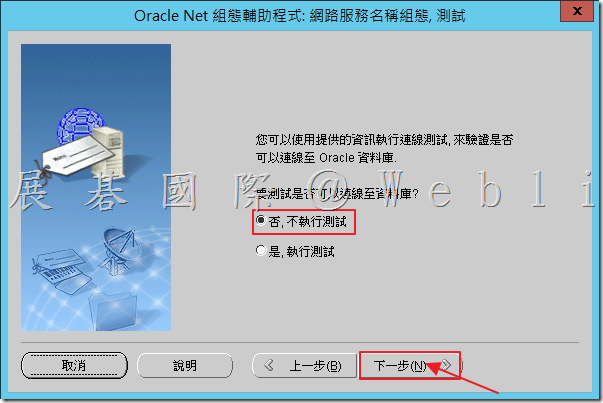
6.7 輸入「網路服務名稱」,接著點選「下一步」。
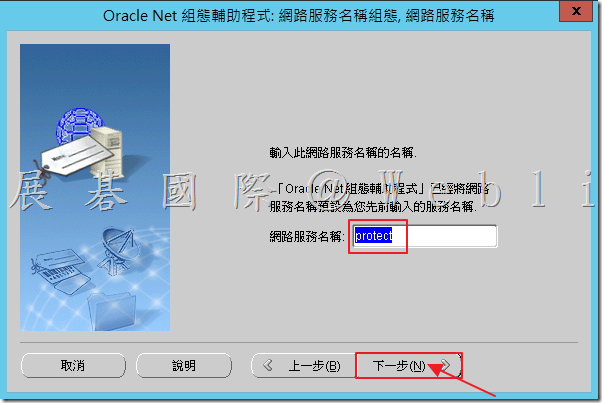
6.8 點選「否」,接著點選「下一步」。
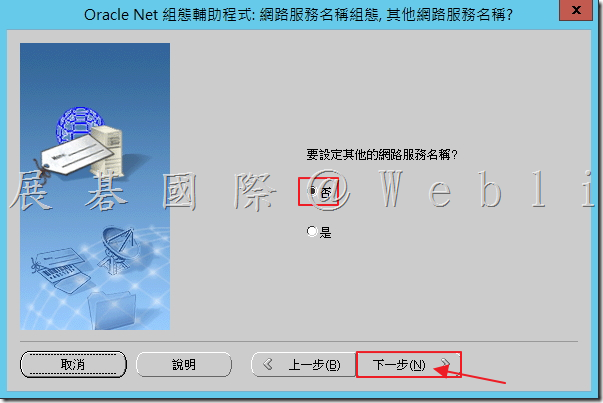
6.9 網路服務組態完成,接著點選「下一步」。
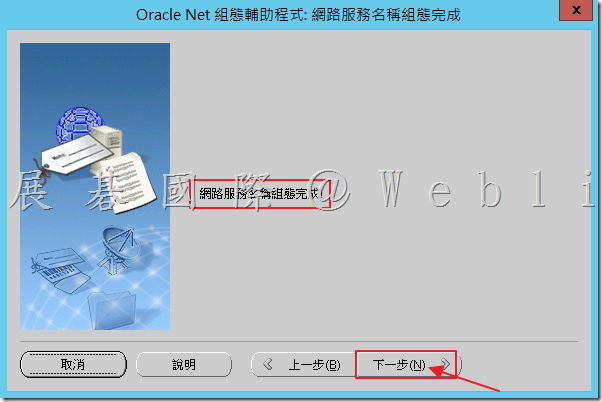
6.10 按下「完成」結束「Oracle 網絡組態輔助程式」。
7. 驗證 Symantec Data Loss Prevention 資料庫。
- 啟動 SQL*Plus → sqlplus /nolog
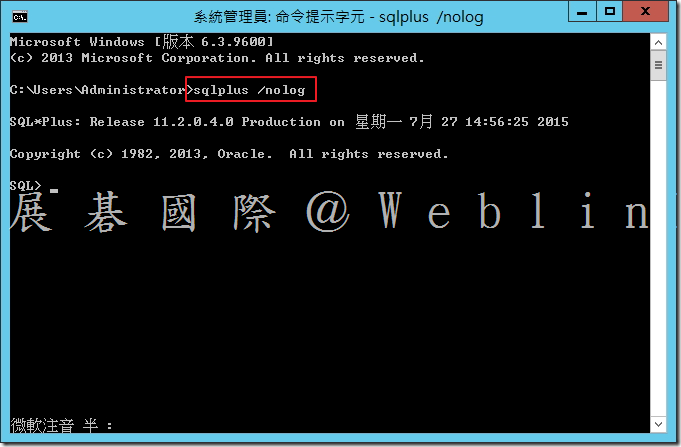
- SYS 使用者身分登入 → SQL> connect sys/password@protect as sysdba
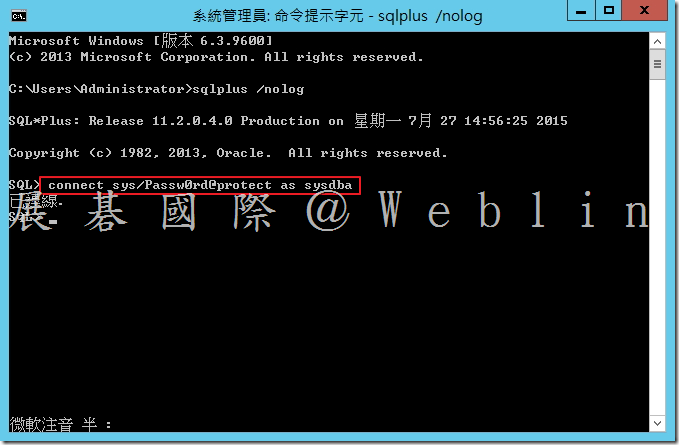
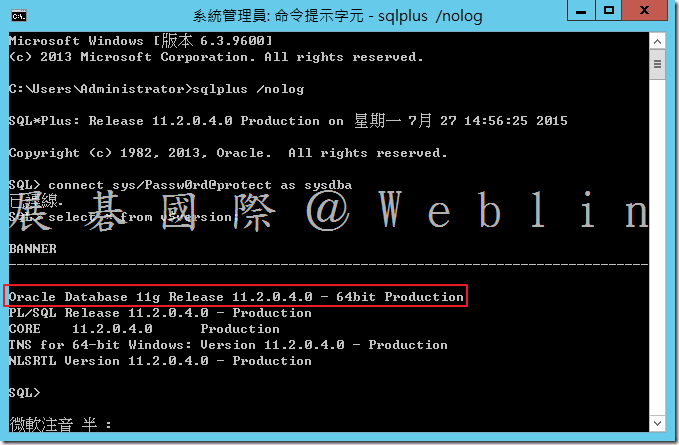
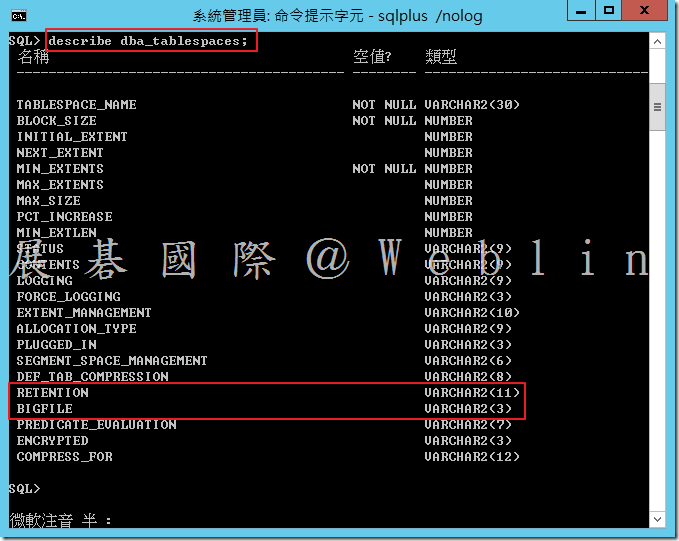
- 執行以下查詢 → SQL> SELECT * FROM v$version;
- 執行以下指令,以描述 dba_tablespaces 檢視 → SQL> describe dba_tablespaces; 檢查輸出是否包含下列資訊﹕RETENTION VARCHAR2(11)、BIGFILE VARCHAR2(3)
8. 為 Symantec Data Loss Prevention 建立 Oracle 使用者帳戶。
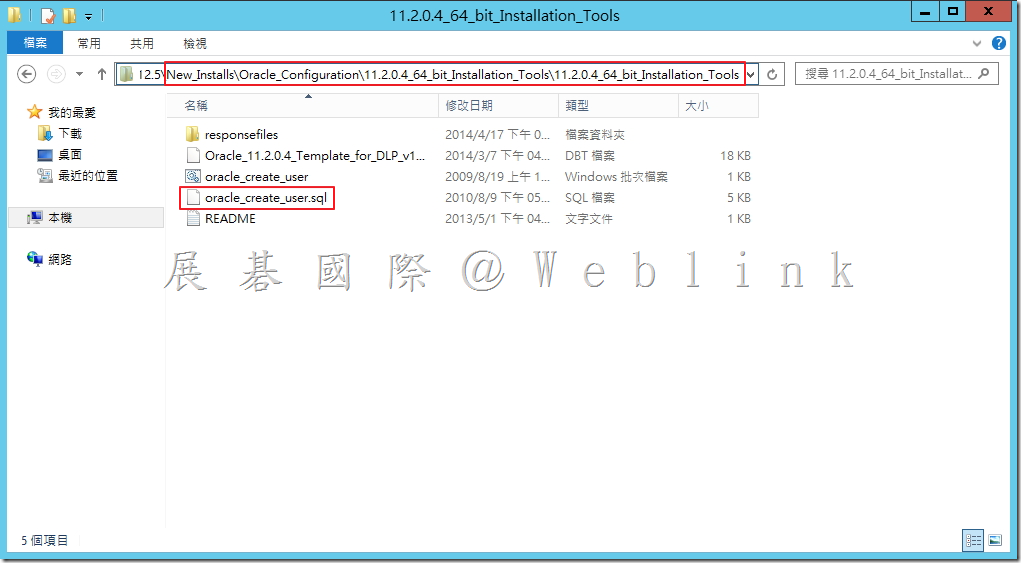
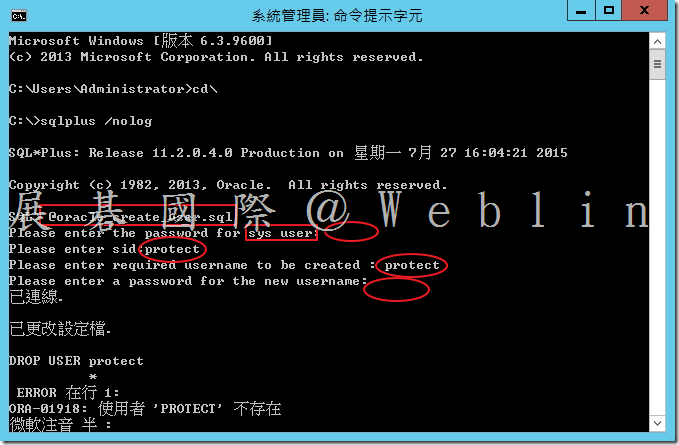
8.1 於「New_Install\Oracle_Configuration\11.2.0.4_64_bit_Installation_Tools
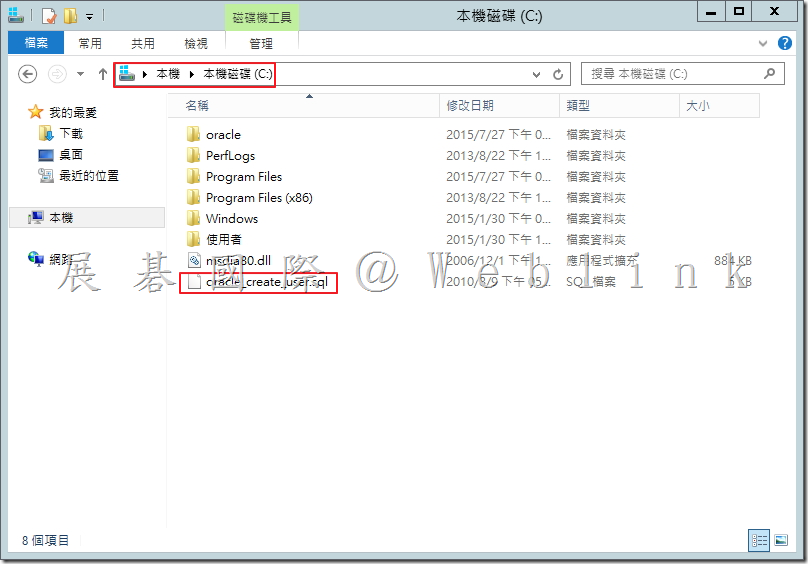
\11.2.0.4_64_bit_Installation_Tools中找到「Oracle_create_user.sql」複製至「c:\」。
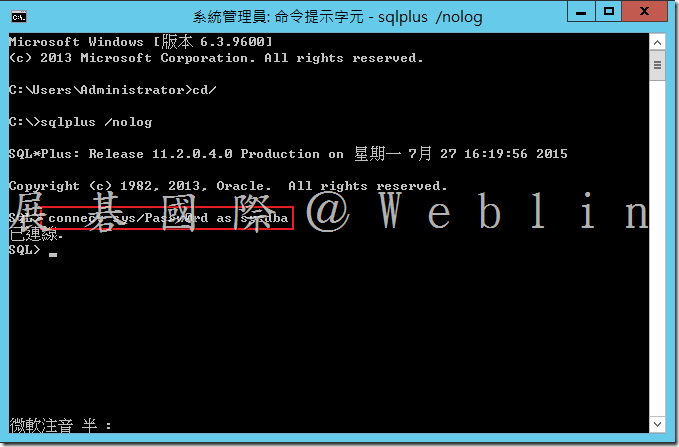
8.2 開啟命令提示字元,切換至「c:\」→ cd\
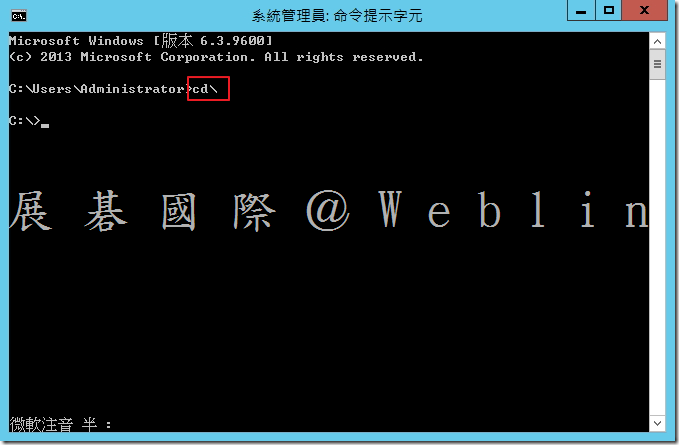
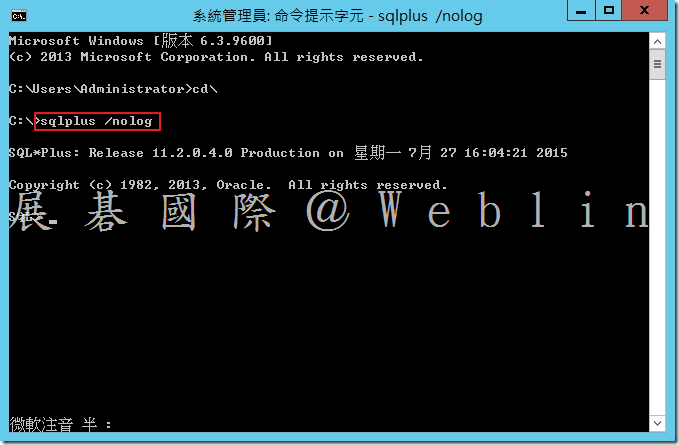
8.3 啟動 SQL*Plus → sqlplus /nolog
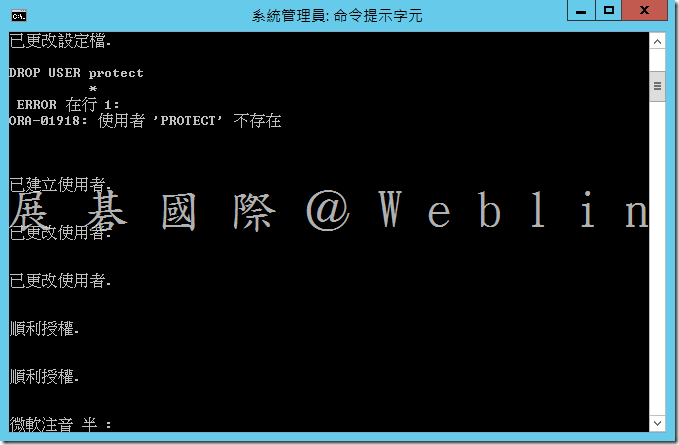
8.4 執行 oracle_create_user.sh 程序檔 → SQL> @oracle_create_user.sql
9. 鎖定 DBSNMP Oracle 使用者帳戶
應鎖定 Oracle DBSNMP 使用者帳戶,以維護安全。
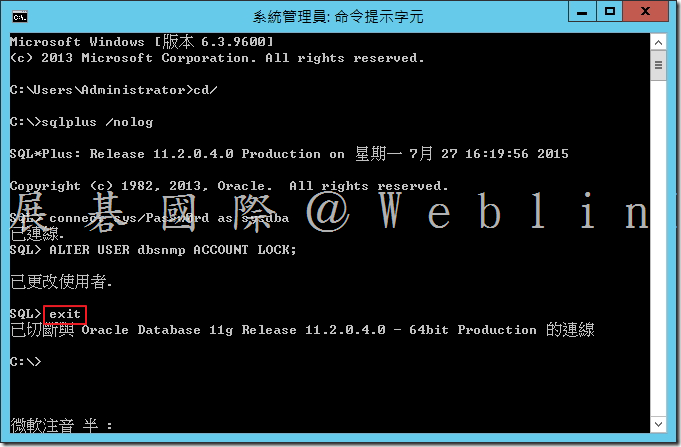
9.1 開啟指令提示字元,然後啟動 SQL*Plus → sqlplus /nolog
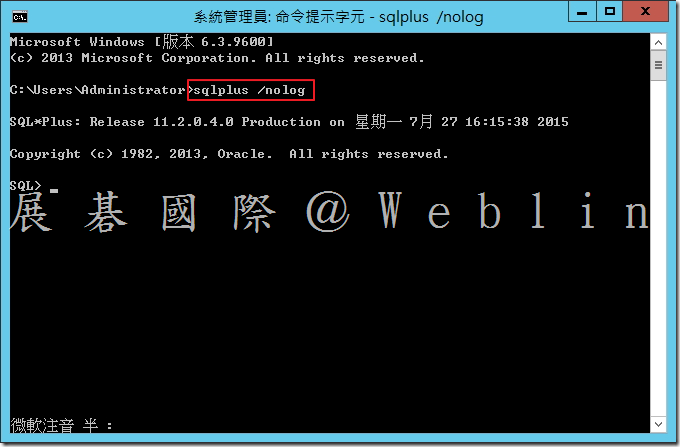
9.2 以SYS使用者身分登入 → SQL> connect sys/password as sysdba
其中 password 為 SYS 密碼。
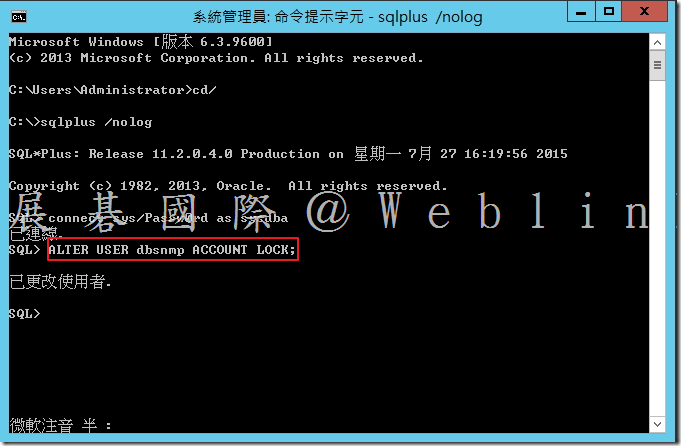
9.3 鎖住 DBSNMP 使用者帳戶 → SQL> ALTER USER dbsnmp ACCOUNT LOCK;
9.4 結束SQL*Plus → SQL> exit
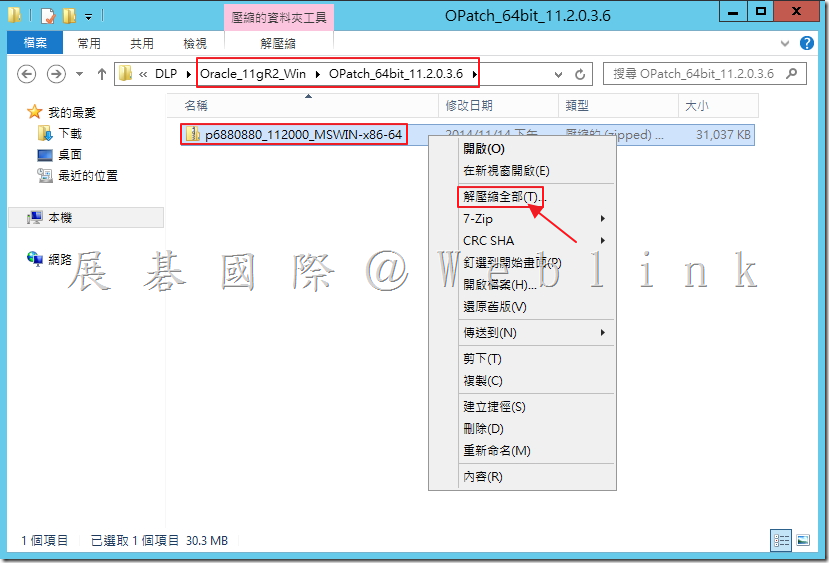
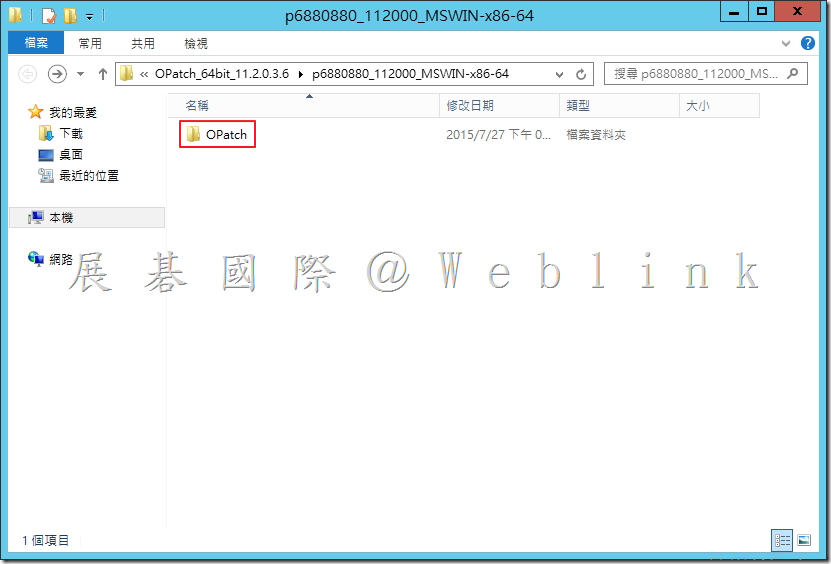
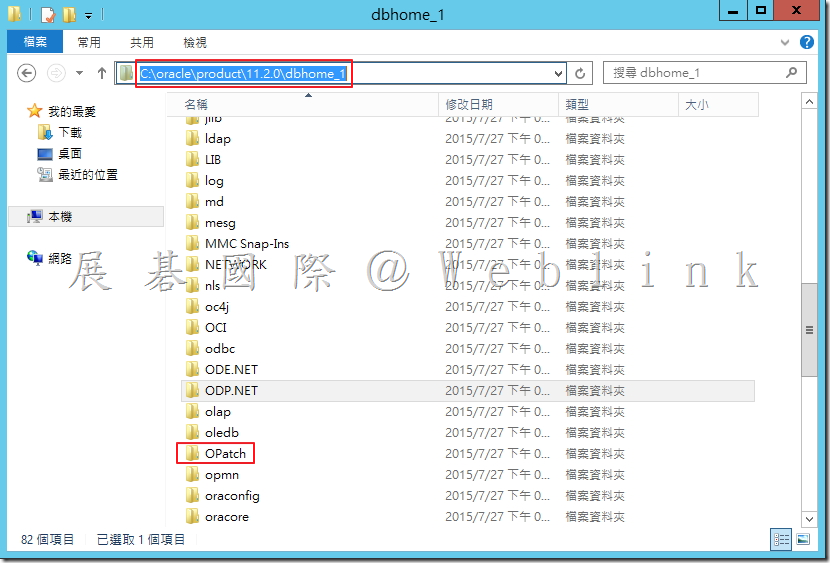
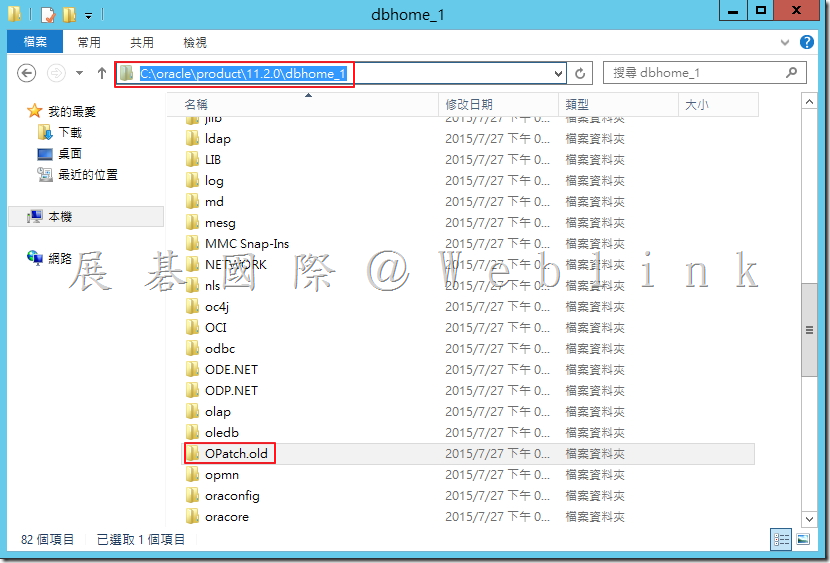












































![clip_image002[1] clip_image002[1]](http://www.wellife.com.tw/symantec/wp-content/uploads/sites/4/2015/07/clip_image0021_thumb.jpg)


![clip_image004[1] clip_image004[1]](http://www.wellife.com.tw/symantec/wp-content/uploads/sites/4/2015/07/clip_image0041_thumb.jpg)