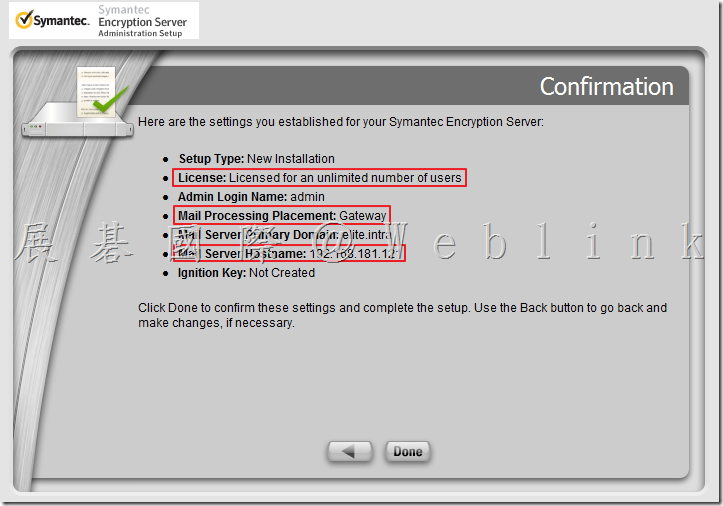
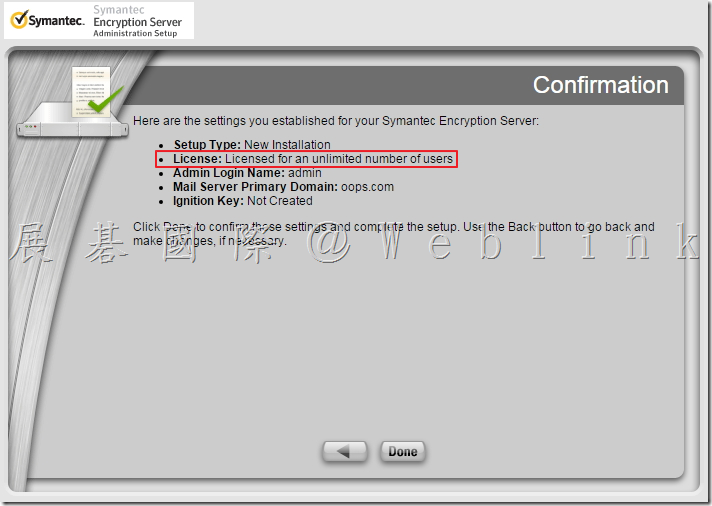
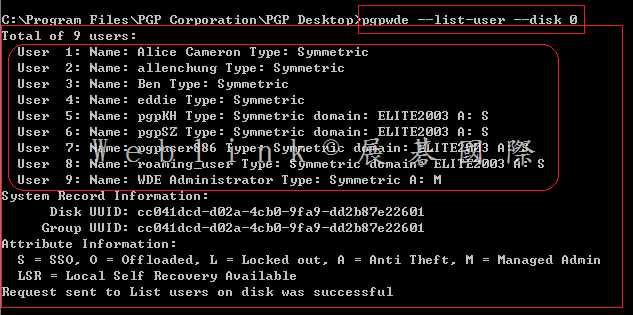
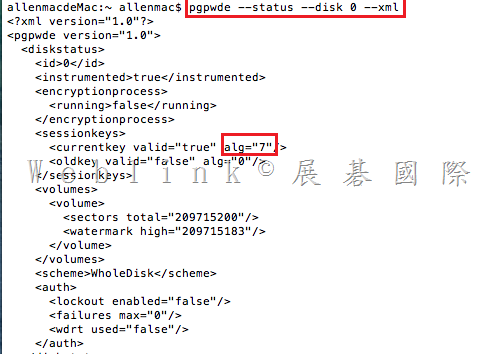
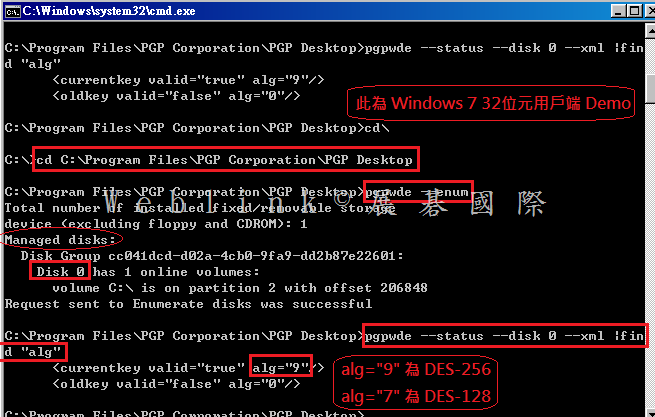
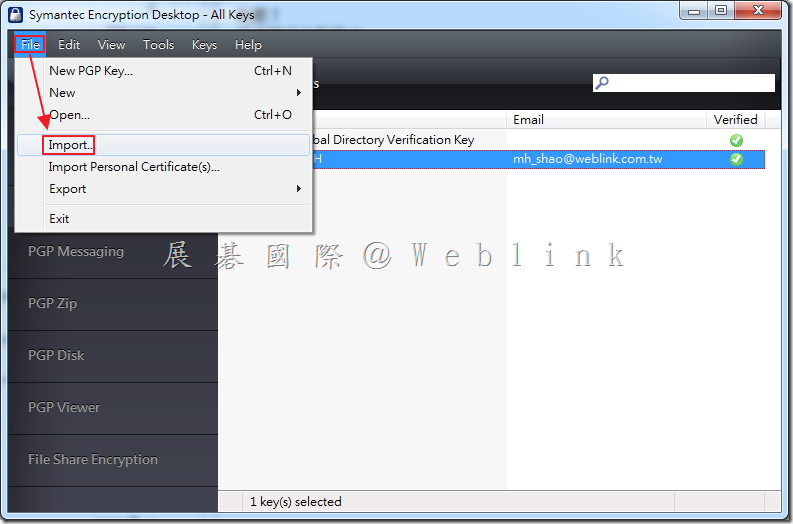
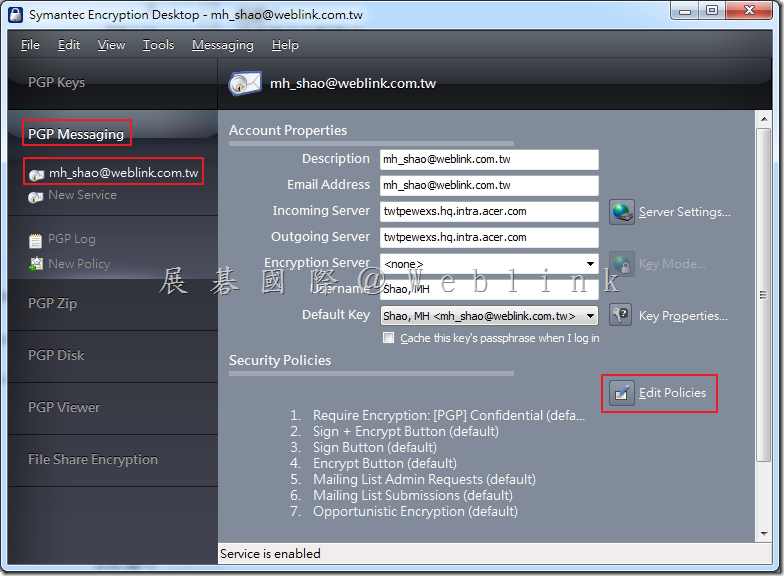
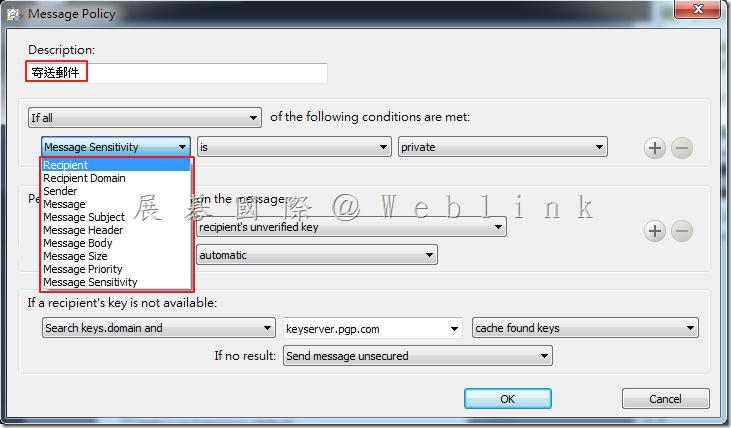
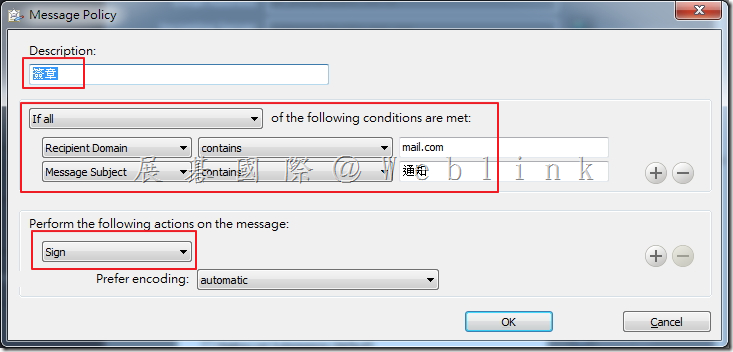
Our company used the Symantec Drive Encryption (managed by Symantec Encryption Management Server (SEMS) and integrate with AD authentication and single sign on).
We always upgrad the Symantec Encryption Management Server (SEMS) to the latest version and it almost works normally.
This time we upgrad the Symantec Encryption Management Server (SEMS) to the (3.3.2 MP10) version.
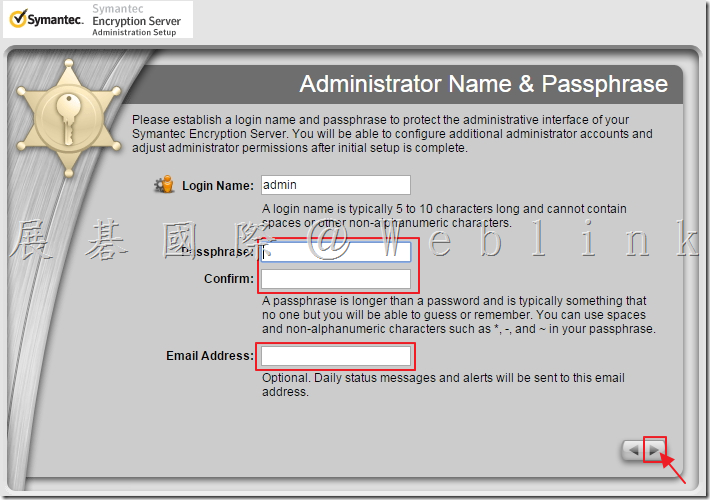
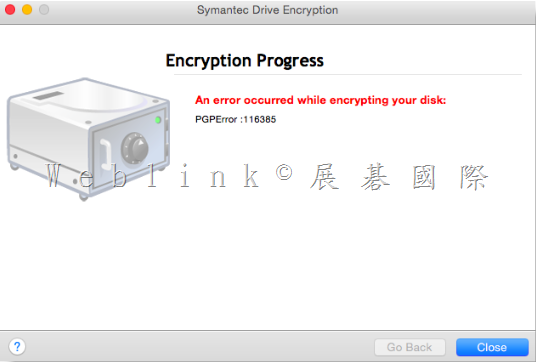
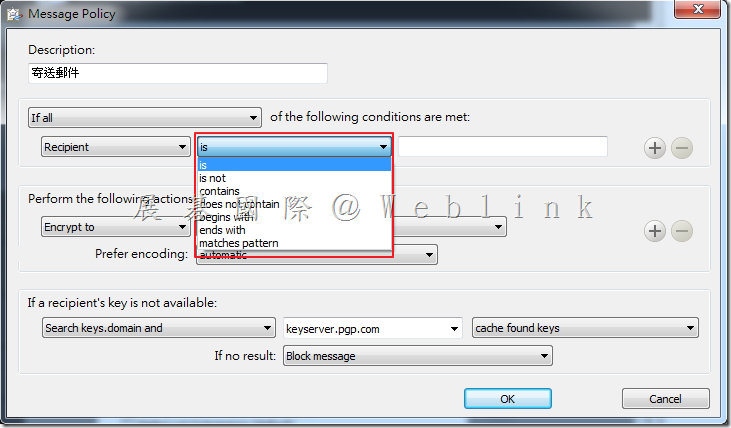
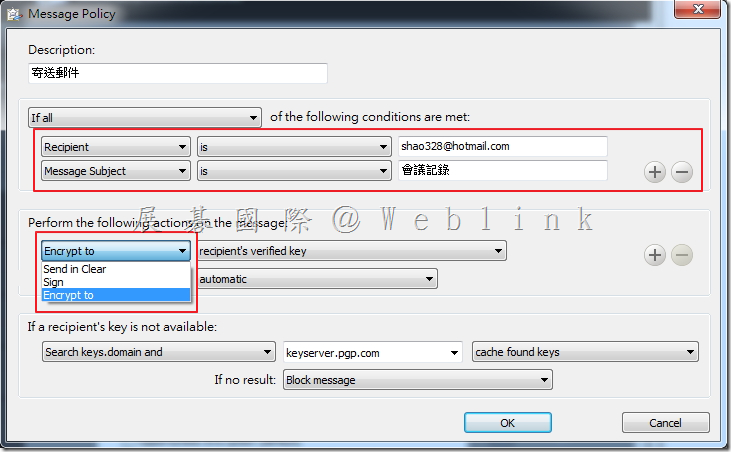
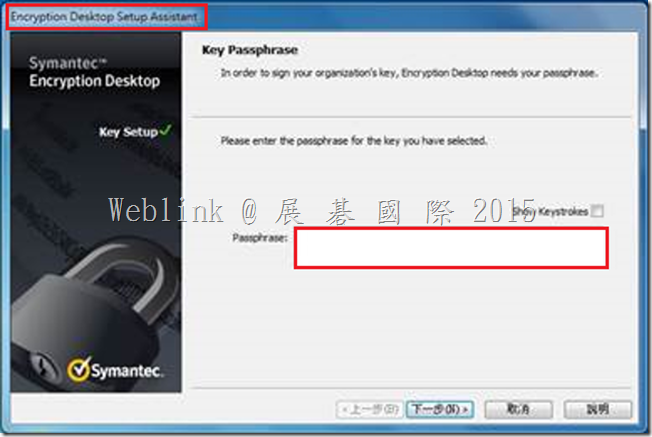
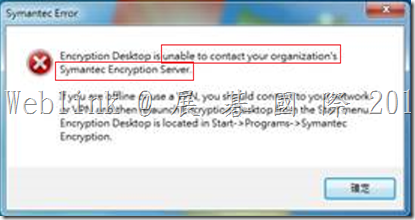
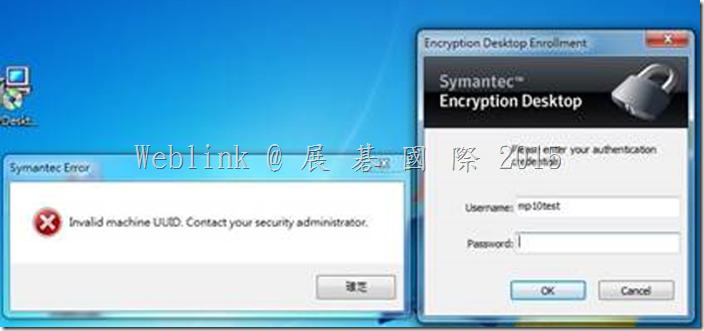
We found if we install a new PC and use the user account (existed in SEMS) to enroll to the SEMS and the Encryption Deaktop Setup Assistant wizard asked to enter the passphrase.
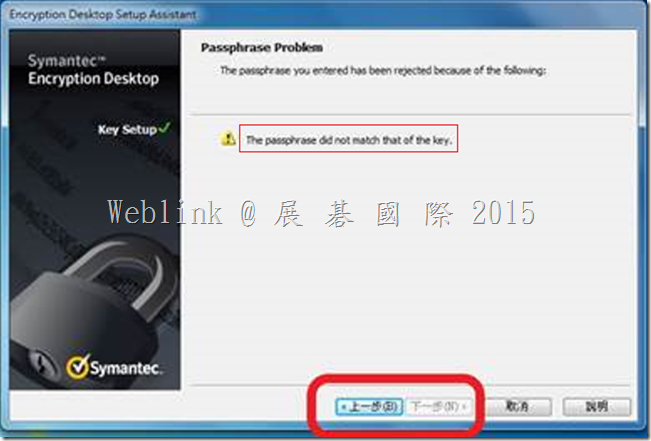
But we can not enter the current domain password (it display “The passprase did not match of the key” ).
It must enter the old domain password (when the user account enrolled to the SEMS first time).
If we didn’t enter the match passphrase we can not press next button.
We refered to the URL below.
It says:
If using Silent Enrollment, we recommend using SKM mode only. Otherwise, a GKM key will be created, using their current Windows passphrase when they first enroll, but the passphrase on that key will not change, so after several Windows passphrase changes, the user will likely not remember the GKM key passphrase.
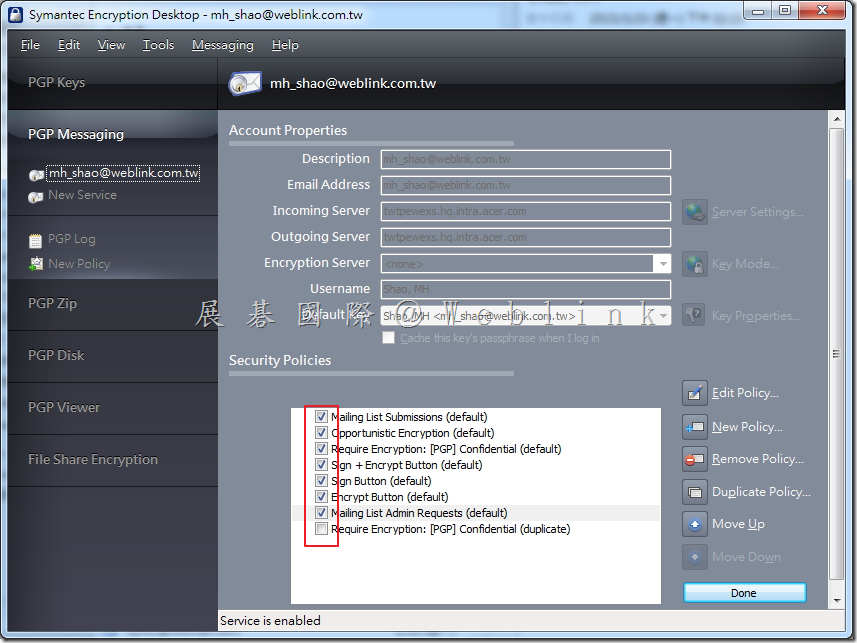
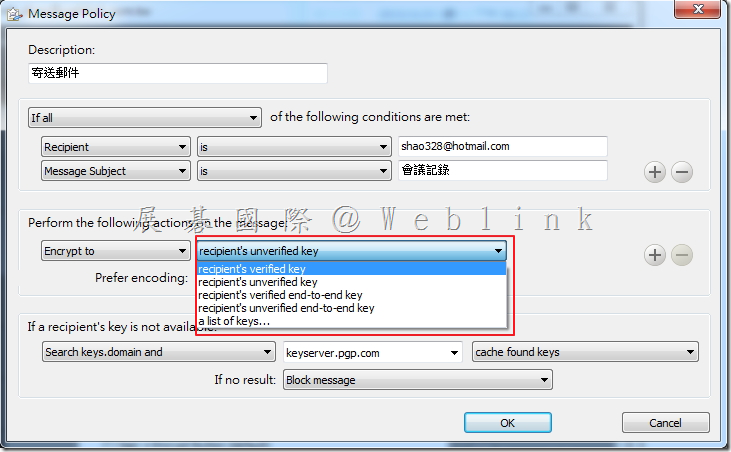
So we unchecked the Guarded Key Mode (GKM) in the key mode setting Under the LAB and the issue solved.
http://www.symantec.com/connect/forums/single-user-issue-multiple-machines
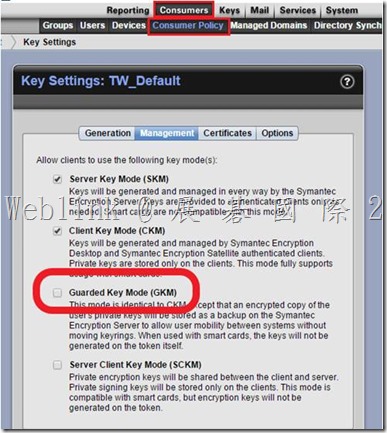
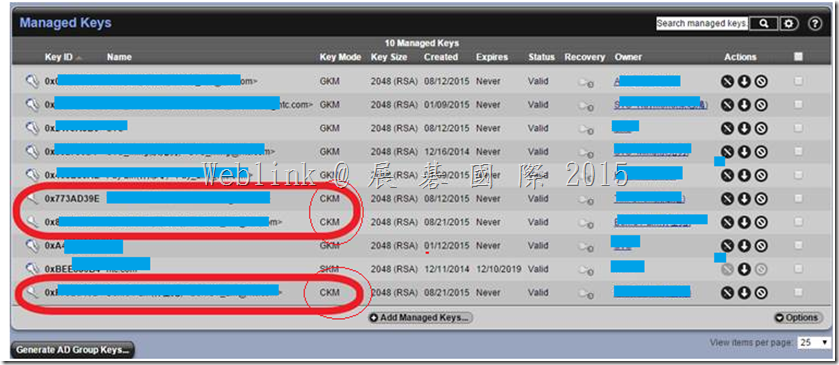
The key mode change to CKM.
1.We want to know why the (3.3.2 MP10) version has this issue?
Our company used the Symantec Drive Encryption (managed by Symantec Encryption Management Server (SEMS) and integrate with AD authentication and single sign on).
【We use the GKM mode】
If we install a new PC and use the user account (existed in SEMS) to enroll to the SEMS and the Encryption Deaktop Setup Assistant wizard asked to enter the passphrase.
The passphrase must be the original one,not the current domain password.
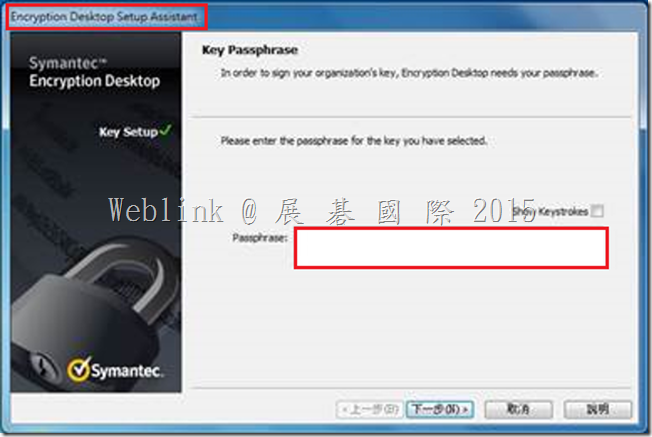
(1) In ( 3.3.2 MP10 )
It display “The passprase did not match of the key”.
And we can not press 【next】 to ignore it,and we can not do any configuration on PGP client.
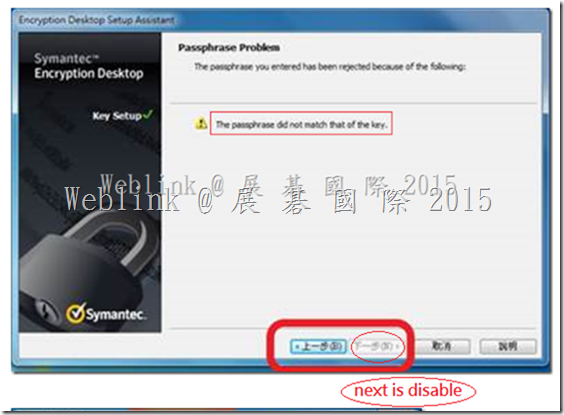
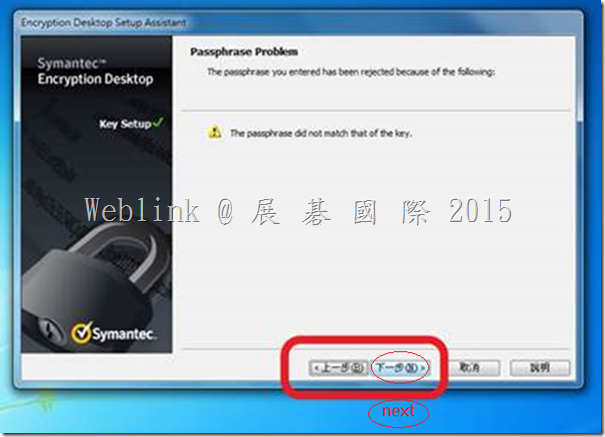
(2) In ( 3.3.2 MP7 and earlier version )
It display “The passprase did not match of the key”.
But we can press 【next】 to ignore it,so we can encrypt th disk.
(3) If we unchecked the GKM then the user key change to CKM.
We install a new PC and use the user account (existed in SEMS) to enroll to the SEMS .
It doesn’t ask to enter the passphrase.
We don’t unchecked the GKM in the production environment because we are not sure what effects will be occured.
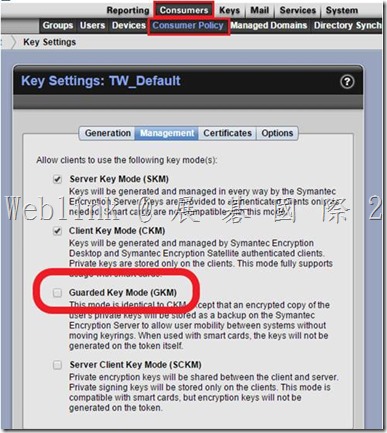
2.What different between check and uncheck the Guarded Key Mode (GKM)?
3.Any effects if we uncheck the Guarded Key Mode (GKM) in the production environment?
4.What is the correct setting for our environment?
【Information form Symantec Connect】
https://www-secure.symantec.com/connect/forums/symantec-drive-encryption-managed-smes-upgrade-332-mp10-issue#comment-form
1. During initial enrollment the users domain password is not used in GKM key mode. The PGP key and passphrase do not have the ability to use SSO(single sign on), the passphrase is assigned to the key in GKM mode when the user manually types their passphrase in the key generation wizard box. This passphrase for the PGP key does not sync with users Windows passwords. If you want to change the passphrase you must do so manually by selecting Symantec Encryption Desktop>PGP Key> Select the key>Change passphrase. It will ask for the old passphrase if it’s not cached and then it will let you update the passphrase.
2. If you are only using Symantec Drive Encryption for your environment, then I would suggest using SKM key mode as this keymode requires that the users don’t need to maintain and remember their passphrase. The Server manages the key and never asks for a passphrase to use these keys. PGP keys have nothing to do with Symantec Drive Encryption unless you manually put them on a Smart Card or Token and then use that for authentication. By default Symantec Drive Encryption uses passphrase user for access and doesn’t require a PGP key to do the intial encryption.
I would recommend you open a support ticket so they can help you figure out a solution to get the users off of GKM key mode. GKM keymode will be problematic since the users don’t use the PGP key. They will forget the passphrase and you will run into an issue attempting to re-enroll or enroll on new machines. I always recommend SKM keymode for Drive Encryption only environments.
I would not recommend you just select CKM keymode since it’s not fixing the issue. It will just add to the confusion in the future. The user will have a keypair that they don’t know or remember the passphrase. There are certain operations that require the users know the passphrase to function properly. I’m very suprised that the enrollment wizard allows you to bypass this section without knowing the passphrase to the key even in CKM mode. That seems like a defect to me since the users will have broken keys if they don’t know the passphrase.