4_SEE RSE Policy
Native policies
- 只能套用至 computer (套用順序:computer、Sub group、Group)
- Native policies are designed for deployment to computers that are not managed by Active Directory.
SEE Roles
- Policy Administrators
- Client Administrators
- Policy Create
SEE 有此兩類 Policy
- 【Active Directory Policy】
- 【Native Policy】
【Active Directory Policy】的畫面
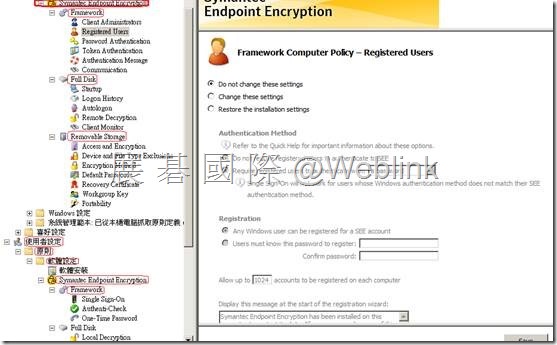
展開【Machine Policy】→【Framework】→來進行以下相關項目的設定
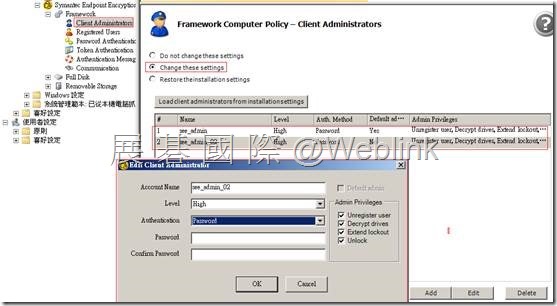
【Client Administrator】
The password must be a minimum of two characters and no longer than 32
Token->P7B file
※ Client Admin 的驗證方式與管理權限 RSE → (用來 Unregister user),FD → (用來 Decrypt drivers、Extend lockout、Unlock)
※ Level →8.0.0 之後用不到
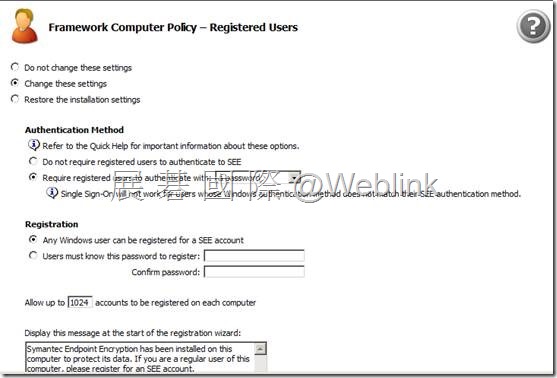
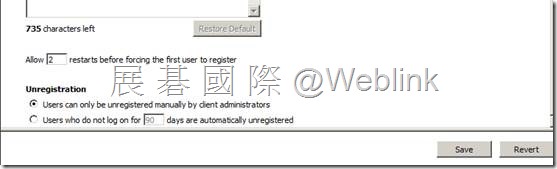
【Registered Users】
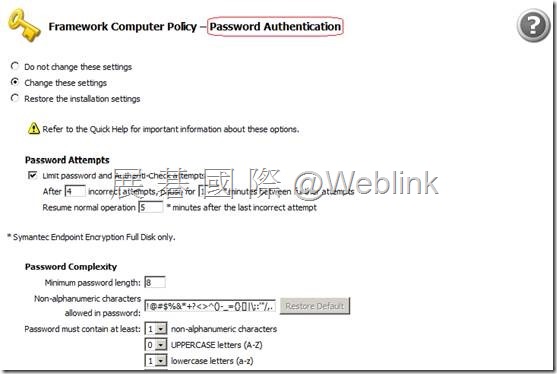
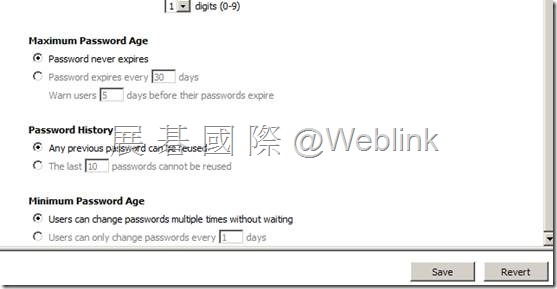
【Password Authentication】
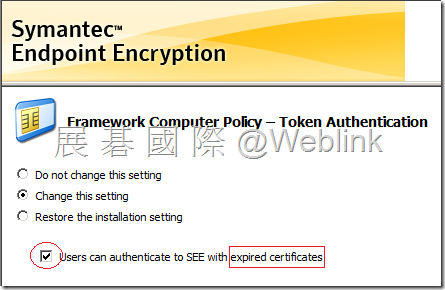
【Token Authentication】
允許過期憑證驗證
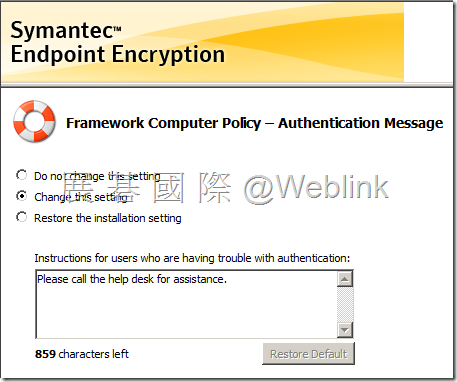
【Authentication Message】
驗證遇到問題時,可依訊息所指定的方式聯繫資訊人員協助處理
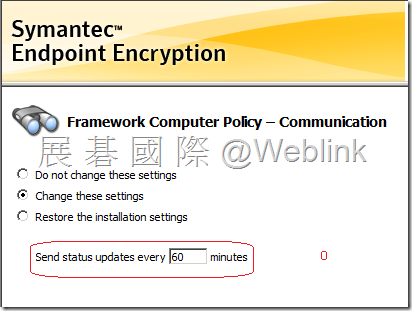
【Communication】
用戶端電腦每隔多久傳送狀態更新給 SEE Management Server
展開【User Policy】→【Framework】→來進行以下相關項目的設定
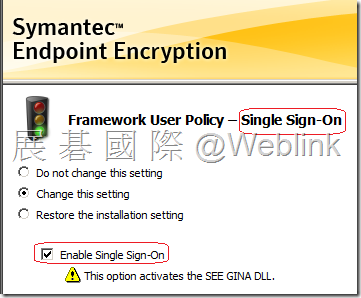
【Single Sign-on】
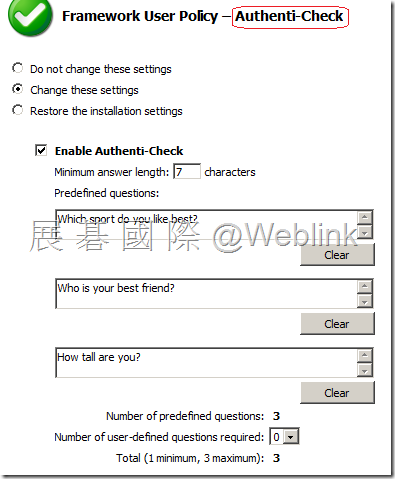
【Authenti-Check】
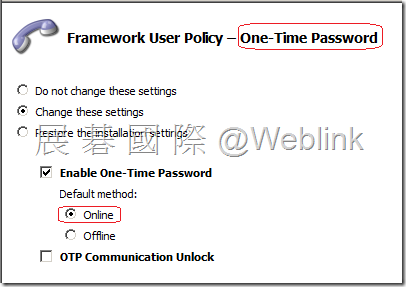
【One-Time Password】
Full Disk 使用者忘記密碼時使用
展開【Machine Policy】→【Removable Storage】→來進行以下 【Removable Storage】 相關項目的設定
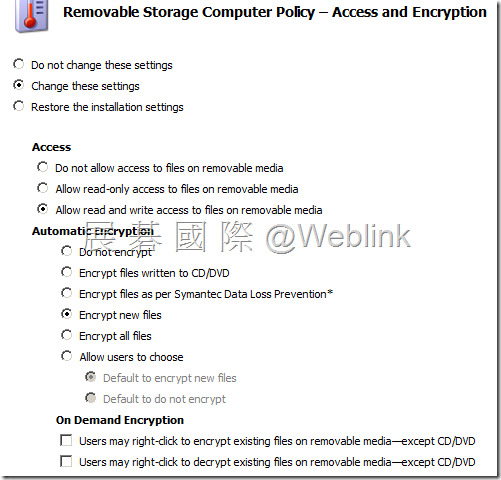
【Access and Encryption】
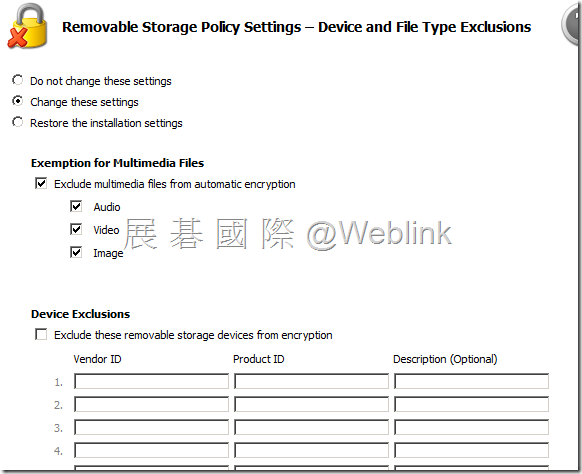
【Device and File Type Exclusions】
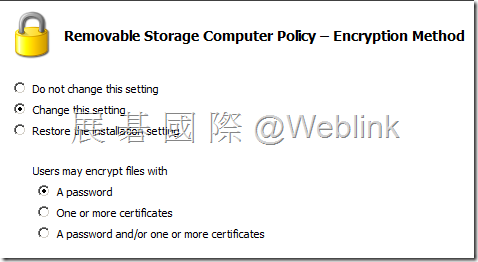
【Encryption Method】
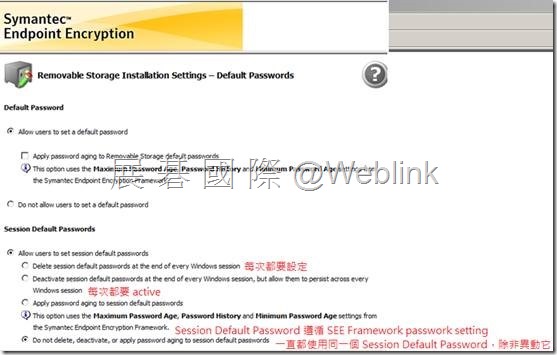
【Default Password】
Session Default Password
可以設定兩個 Session Default Password
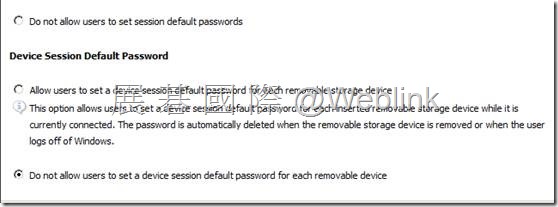
Device Session Default Password
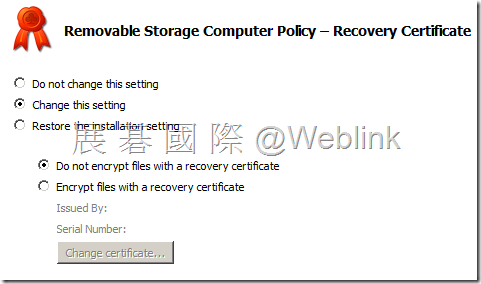
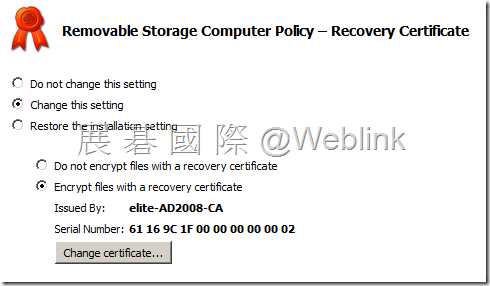
【Recovery Certificate】
|
http://www.symantec.com/connect/forums/password-recovery-encrypted-files If you have a master certificate, you may. 1. Launch MMC, add Certificates snap-in for my user account. Now create the Removable storage client package. In the Removable Storage Installation Settings –Encryption Method, select A password or A password and/or one or more certificates. In the Removable Storage Installation Settings –Recovery Certificate, choose Encrypt files with a recovery certificate and browse and select the saved P7B certificate. In the Removable Storage Installation Settings – Portability pane check Copy the Removable Storage Access Utility to all removable storage devices. |
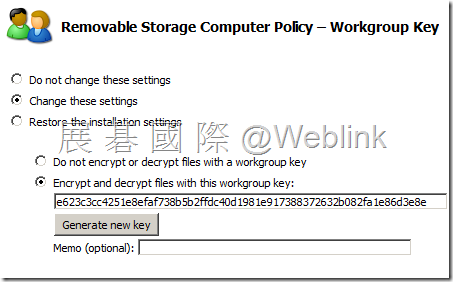
【Workgroup Key】
【Portability】
展開【Machine Policy】→【Full Disk】→來進行以下 【Full Disk】 相關項目的設定
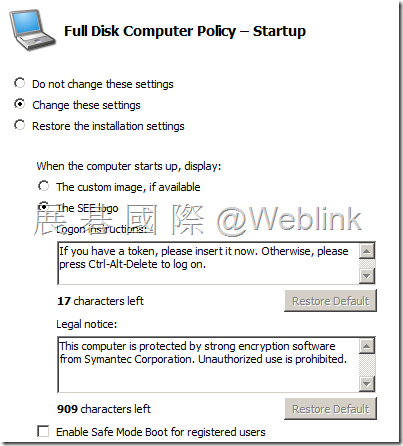
【Startup】
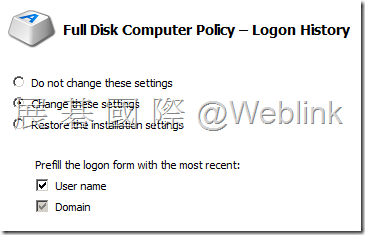
【Logon History】
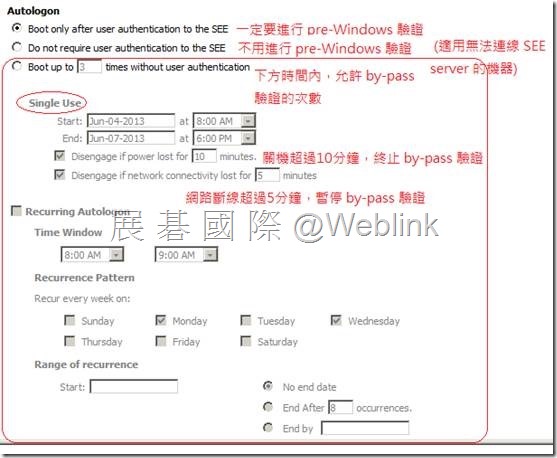
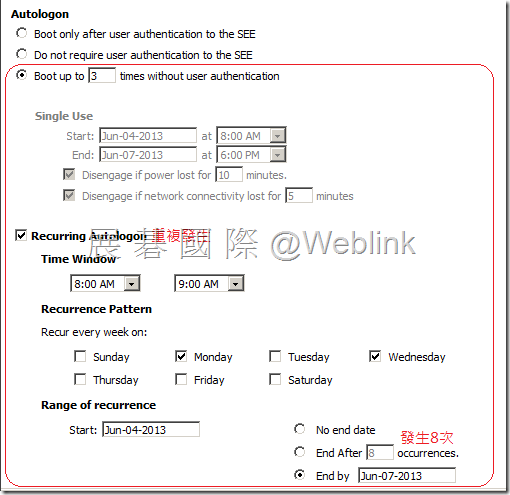
【Autologon】client 收到 policy 後要5分鐘才生效
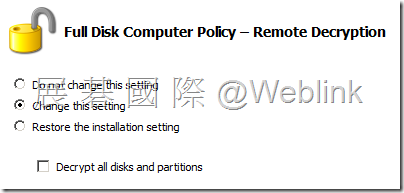
【Remote Decryption】
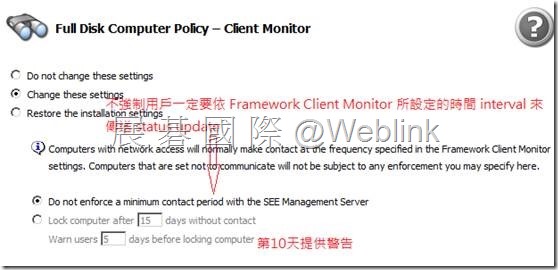
【Client Monitor】
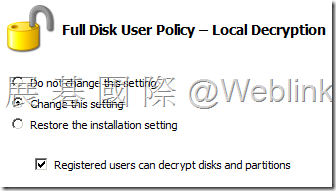
【Local Decryption】

![clip_image015[1] clip_image015[1]](http://www.wellife.com.tw/symantec/wp-content/uploads/sites/4/2013/10/clip_image0151_thumb.png)