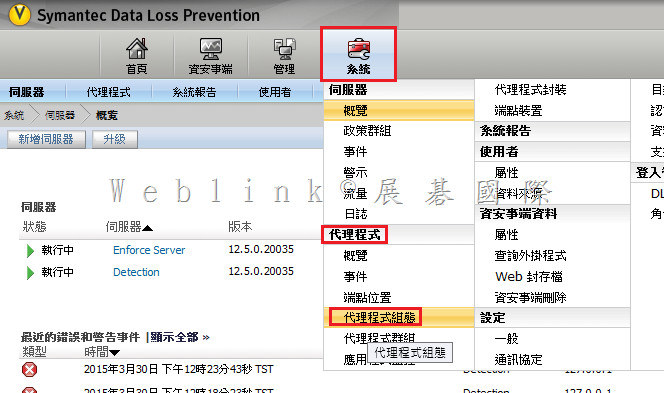
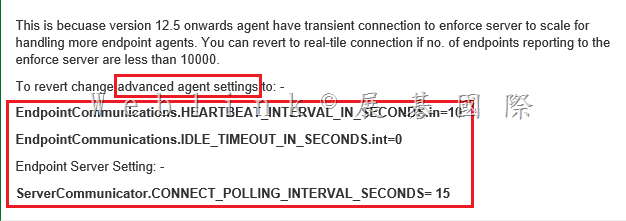
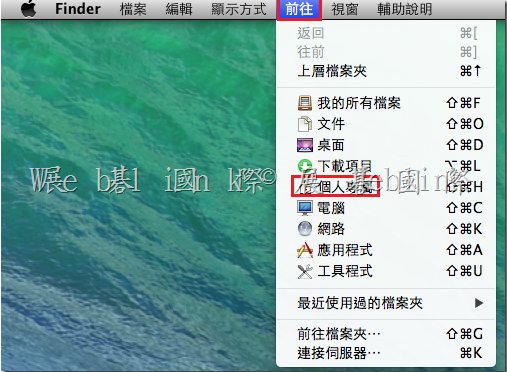
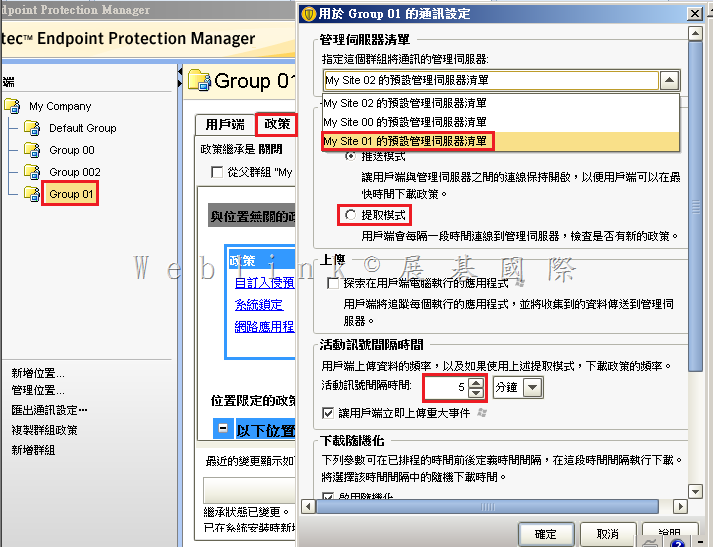
安裝好 PGP Desktop E-mail 後,outlook 無法發信出現【PGP Universal service not available】
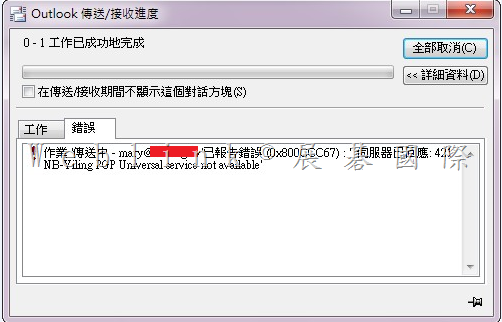
請將 Outgoing Mail Server (SMTP) 中,SSL/TLS 下拉改選【Do not attempt】即可解決
[點圖可放大]
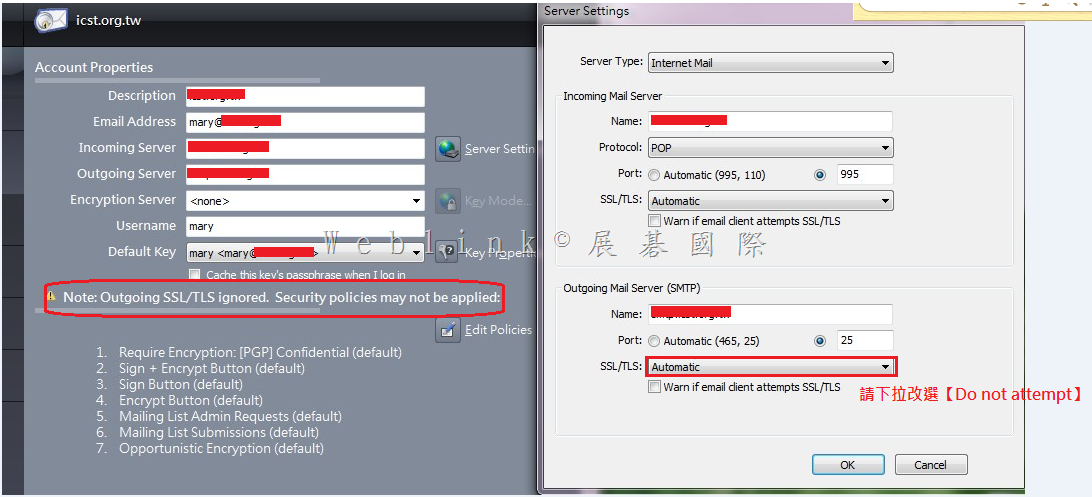
【其他的除錯步驟】
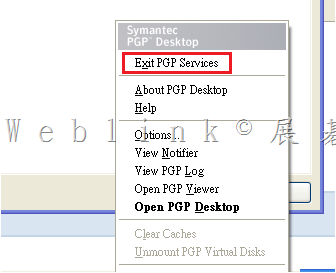
1.Exit PGP Services 後,確認 Outlook 寄信是否正常,若仍不正常則可能是原始 mail client 設定有問題
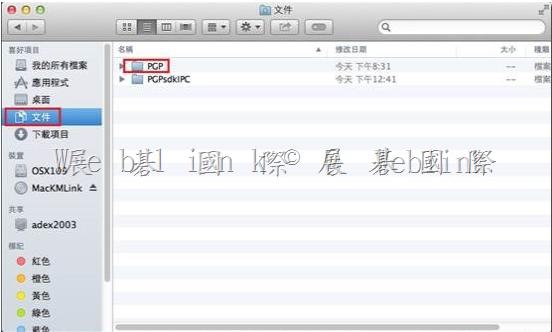
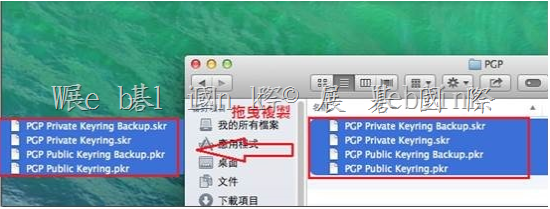
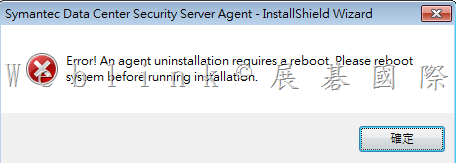
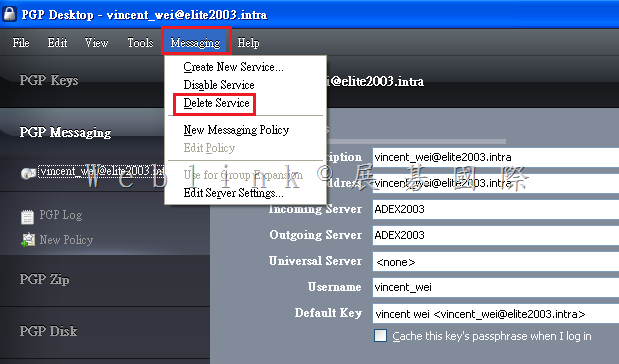
2. 刪除重建 PGP Desktop E-mail service
3.提供用戶端 log
4.Enterprise Support – Symantec Corp. – Troubleshooting: PGP Messaging Services for PGP Desktop 10 for Windows
http://www.symantec.com/business/support/index?page=content&id=TECH149647
By default, PGP Desktop automatically determines your email account settings and creates a PGP Messaging service that proxies messaging for that email account.
Because of the large number of possible email account settings and mail server configurations, on some occasions a messaging service that PGP Desktop automatically creates may not work quite right.
If PGP Desktop has created a messaging service that is not working right for you, one or more of the following items may help correct the problem:
Verify that you can both connect to the Internet and send and receive email with PGP Services stopped. To do this:
Right-click the PGP Desktop Tray icon and select Stop PGP Services from the list of commands.
Note: You should always restart your email client after starting or stopping PGP Services.
Read the PGP Desktop Release Notes for the version of PGP Desktop you are using to see if your problem is a known issue.
Make sure SMTP authentication is enabled for the email account (in your email client). This is recommended for PGP Desktop to proxy your messaging. If you only have one email account and you are not using PGP Desktop in a PGP Universal Server-managed environment, then SMTP authentication is not needed. It is required when using a PGP Universal Server as your SMTP server, or when you have multiple email accounts on the same SMTP server.
Open the PGP Log to see if the entries offer any clues as to what the problem might be.
If SSL/TLS is enabled in your email client, you must disable it there if you want PGP Desktop to proxy your messaging. (This does not leave the connection to and from your mail server unprotected; by default PGP Desktop automatically attempts to upgrade any unprotected connection to SSL/TLS protection. The mail server must support SSL/TLS for the connection to be protected.)
If either Require STARTTLS or Require SSL is selected (in the SSL/TLS settings of the Server Settings dialog box) your mail server must support SSL/TLS or PGP Desktop will not send or receive any messages.
If your email account uses non-standard port numbers, make sure these are included in the settings of your messaging service.
If PGP Desktop is creating multiple messaging services for one email account, use a wild card for your mail server name.
Delete the PGP Messaging service that is not working correctly and send/receive email. PGP Desktop regenerates the messaging service.
If none of these items help correct the problem, try manually creating a PGP Messaging Service.
5.
http://www.symantec.com/connect/forums/not-working-outbound-mail-encryption-outlook-2010-pgp-1021
Please reread the PGP Release Notes for any known conflict or settings adjustments that may be needed for your system.
Although I don’t see Norton 360 specifically mentioned, the following quote may offer guidance that might also help with Norton 360 use.
Symantec Norton AntiVirus 9.x through 10.x, Symantec Norton Internet Security 2003, Symantec Norton Internet Security 2004
Disable email scanning.
For Norton Internet Security users, disable Norton Privacy Control and Spam Alert.
Disable SSL/TLS in Server Settings in PGP Desktop and PGP Universal Satellite. (In PGP Desktop, select the PGP Messaging Control Box and then choose Messaging > Edit Server Settings. For SSL/TLS, select Do Not Attempt. In PGP Universal Satellite, on the Policies tab, select Ignore SSL/TLS.) These versions of Norton AntiVirus prevent all mail clients from using SSL/TLS, regardless of the use of PGP software.
Symantec Norton AntiVirus 11.x through 12.x, Symantec Norton Internet Security 2005, Symantec Norton Internet Security 2006
No special configuration required for MAPI email.
When using POP email, enable Auto-Protect and disable the Anti-Spam and Email Scanning options. Auto-Protect, which is enabled by default, provides protection against viruses in email messages when the message is opened.
Disable SSL/TLS in Server Settings in PGP Desktop or PGP Universal Satellite. (In PGP Desktop, select the PGP Messaging Control Box and then choose Messaging > Edit Server Settings. For SSL/TLS, select Do Not Attempt. In PGP Universal Satellite, on the Policies tab, select Ignore SSL/TLS.) These versions of Norton AntiVirus prevent all mail clients from using SSL/TLS, regardless of the use of PGP software.